- SAP Community
- Products and Technology
- CRM and Customer Experience
- CRM and CX Blogs by SAP
- SAP Variant Configuration and Pricing - How to wor...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
SAP Variant Configuration and Pricing writes the following audit logs:
- Security event logs when a user tries to logon to the administration UI with the wrong password or when someone tries to call the configuration and pricing services with an invalid oauth token.
- Configuration change logs for each relevant setting that is changed by the customer or by SAP operations through the administration UI.
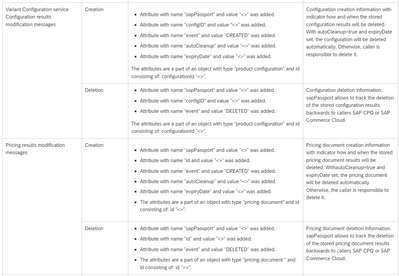
Furthermore, each creation and each deletion of a configuration or pricing document (through the corresponding endpoints of the configuration and pricing services) is logged:
Those logs also contain the so-called SAP Passport, which can tell you if the service endpoint was called from SAP Commerce Cloud or from SAP CPQ.
The fields autoCleanup=true and the expiryDate in those logs tell you when the configuration or pricing document will be deleted automatically.
Please refer to the Security Guide for SAP Variant Configuration and Pricing to find a list of all kinds of written logs: Audit Logging | SAP Help Portal
SAP Variant Configuration and Pricing uses the SAP Audit Log service on SAP BTP: Audit Logging in the Cloud Foundry Environment | SAP Help Portal
Please note that there are two different views on the audit logs:
- Consumer view (used by customers): User ids of customer users are visible, while user ids of SAP operations users are anonymized.
- Provider view (used by SAP): User ids of customer users are anonymized, while user ids of SAP operations users are visible.
Audit logs are kept for 90 days.
How to get access to the audit logs?
You can either use the Audit Log Viewer or the Audit Log Retrieval API.
Audit Log Viewer
To use the audit log viewer, open your BTP subaccount, go to the menu Entitlements, press the Edit button, press the Add Service Plans button, search for the Audit Log Viewer Service, choose its plan free (Application), press the button Add 1 Service Plan, and the press button Save.
Go to the menu Services → Service Marketplace in the same subaccount, search for Audit Log Viewer Service, open the corresponding tile and press the Create button. Press the Create button in the popup dialog. Press View Subscription in the next popup dialog to switch to the menu Services → Instances and Subscriptions. There, you should see the application Audit Log Viewer Service with the plan free next to the application SAP Variant Configuration and Pricing.
Go to the menu Security → Role Collections in the same subaccount, create a new role collection with the name Audit Log Viewer. Open the new role collection, press the Edit button, assign the role(s) Auditlog_Auditor to the role collection and assign your user, usually the email address, to the role collection and press the Save button.
With that, you can use the audit log viewer: Go to the menu Services → Instances and Subscriptions, open the Audit Log Viewer Service and press the Go to Application button.
Audit Log Viewer 1.0 opens with prefilled From-Date and To-Date filters, but empty search results list. Press Reload button to start the search. You should see all audit logs written for that subaccount in the selected time frame. You should for example see logs for the changes to the role collection that were done above. You can use the other filter input field to further restrict that list.
The audit log viewer only shows the first 500 hits based on the chosen from- and to-date filters.
Audit Log Retrieval API
The limitation in the audit log viewer of maximum 500 logs and its limited filter capabilities are problematic when you, for example, want to find out when a certain configuration or price document was created or deleted.
In that case, you must use the Audit Log Retrieval API, store the logs in a file, and analyze the logs there:
Create an instance of the service Audit Log Management:
- In the SAP BTP Cockpit Account Explorer choose your account
- Search and find your subaccount there and navigate to your space/org (if no org , create a new space/org for this subaccount)
- From the navigation menu of the subaccount choose Services → Service Marketplace
- Search for the Audit Log Management Service and open the tile
- Press the Create button
- In the popup dialog choose runtime environment Cloud Foundry and the created space and enter an instance name like auditlogs. Press the Create button to close the dialog.
Create a service key for that service instance:
- Go to the menu Services → Instances and Subscriptions and click on the created instance to open it
- Press the Create button in the Service Keys section
- Enter a service key name and press the Create button
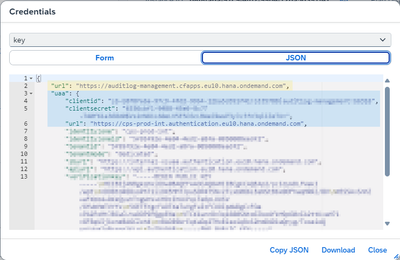
- Click on View Credentials to open the service key details
- Find the service url, uaa url, client id, and client secret:
Do the service call:
- You should be able to see the service key details now. From there, take note of uaa.url, uaa.clientid, uaa.clientsecret and url.
- Generate an oauth token using the uaa.url, uaa.clientid, and uaa.clientsecret:
URL: <value of "uaa.url">/oauth/token?grant_type=client_credentials
Method: POST
Authentication Method: Basic Authentication
Username: <Value of "uaa.clientid">
Password: <Value of "uaa.clientsecret"> - From the response get the access_token and use it as Bearer token for the following GET request:
<url (from service key)>/auditlog/v2/auditlogrecords
Method : GET
Authorization Bearer <access_token> - Get the audit logs filtered by time (using from and to time):
<url (from service key)>/auditlog/v2/auditlogrecords?time_from=2024-02-20T00:00:01&time_to=2024-02-20T23:59:59
Method : GET
Authorization Bearer <access_token> - Check the response header for the field paging. To get the next chunk of logs, call:
<url (from service key)>/auditlog/v2/auditlogrecords?handle=<handle from last paging response header>
Method : GET
Authorization Bearer <access_token>
After doing all the above steps, you should be able to get the service response in JSON format with all the audit logs related to that subaccount.
Online docu: Audit Log Retrieval API Usage for Subaccounts in the Cloud Foundry Environment | SAP Help Portal
API docu: SAP Business Accelerator Hub
PowerShell script to extract the audit logs
# (!)Before running the script:
# replace placeholders <> for $uaaUri, $clientId, $clientSecret, and $uri (get them from service key)
# adapt the time_from- and time_to-timestamps in $query
# get oauth token
# ---------------
$uaaUri = "<region-specific uaa authentication host>/oauth/token?grant_type=client_credentials"
$clientId = "<your client id>"
# use single quotes here otherwhise it will not work in PowerShell because of potential $ sign in the client secret string:
$clientSecret = '<your client secret>'
$user = $clientId
$pw = $clientSecret
$pair = "$($user):$($pw)"
$encodedCredentials = [System.Convert]::ToBase64String([System.Text.Encoding]::ASCII.GetBytes($pair))
$headers = @{ "Authorization" = "Basic $encodedCredentials" }
$response = Invoke-WebRequest -Uri $UaaUri -Method POST -Headers $headers
$token = (ConvertFrom-Json $response.Content).access_token
# read the audit logs and write to file:
# --------------------------------------
# Canary
# $uri = "https://auditlog-management.cfapps.sap.hana.ondemand.com/auditlog/v2/auditlogrecords"
$uri = "<region-specific auditlog service host>/auditlog/v2/auditlogrecords"
$query = "time_from=2024-02-20T00:00:01&time_to=2024-02-20T23:59:59"
$headers = @{ "Authorization" = "Bearer " + $token; 'Accept' = 'application/json'}
$uri1 = $uri + '?' + $query
$response = Invoke-WebRequest -Uri $uri1 -Headers $headers
# uncomment to print in console:
#$response.statusCode
#$response.Headers.paging
if ($response.statusCode -eq 200) {
$response.RawContent | Out-File -FilePath .\audit-logs.txt
# read remaining audit logs:
while ($response.Headers.containsKey("paging")) {
$uri2 = $uri + '?' + $response.Headers.paging
$response = Invoke-WebRequest -Uri $uri2 -Headers $headers
if ($response.statusCode -eq 200) {
$response.RawContent | Out-File -FilePath .\audit-logs.txt -Append
} else { break }
}
# uncomment to display file content:
# Get-Content -Path .\audit-logs.txt
}
::from https://blog.danskingdom.com/allow-others-to-run-your-powershell-scripts-from-a-batch-file-they-will-love-you-for-it/
@ECHO OFF
CLS
SET ThisScriptsDirectory=%~dp0
SET PowerShellScriptPath=%ThisScriptsDirectory%MyPowerShellScript.ps1
PowerShell -NoProfile -ExecutionPolicy Bypass -Command "& '%PowerShellScriptPath%'";
- SAP Managed Tags:
- SAP Variant Configuration and Pricing
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
Business Trends
270 -
Business Trends
13 -
chitchat
1 -
customerexperience
1 -
Event Information
256 -
Event Information
18 -
Expert Insights
30 -
Expert Insights
52 -
Life at SAP
133 -
Life at SAP
1 -
Product Updates
666 -
Product Updates
32 -
SAP HANA Service
1 -
SAPHANACloud
1 -
SAPHANAService
1 -
Technology Updates
453 -
Technology Updates
15
- Big Update on the e-learning “Integrating SAP Sales Cloud and SAP Service Cloud with SAP S/4HANA" in CRM and CX Blogs by SAP
- Utility Product Integration Layer (UPIL) in S/4HANA Utilities for Customer Engagement – Part 1 in CRM and CX Blogs by Members
- Maximize Results and Drive Sustainability in Fashion Retail with SAP and GK AIR Dynamic Pricing in CRM and CX Questions
- SAP variant configuration and pricing - manual exchange rate for a quote from SAP CPQ in CRM and CX Questions
- What is planned for the 2405 release of SAP Variant Configuration and Pricing? in CRM and CX Blogs by SAP
| User | Count |
|---|---|
| 8 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |