
- SAP Community
- Products and Technology
- Enterprise Resource Planning
- ERP Blogs by SAP
- RISE with SAP: ‘Defense in Depth’ Security Archite...
Enterprise Resource Planning Blogs by SAP
Get insights and updates about cloud ERP and RISE with SAP, SAP S/4HANA and SAP S/4HANA Cloud, and more enterprise management capabilities with SAP blog posts.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-12-2021
12:04 PM
(Jana Subramanian is APJ Principal Cybersecurity Advisor for Cloud Security and Fellow of Information Privacy (FIP) awarded by International Association of Privacy Professional (IAPP). Jana supports strategic customer engagements on cybersecurity, data privacy, multi-cloud security architecture, contractual assurance, audit, and compliance domains.)
Introduction
The SAP S/4HANA Cloud is at the core of “Rise with SAP” offering. For a customer, it holds mission critical data used to implement business processes and data analytics. It is deployed in a public cloud as SaaS (Software-as-a-Service) offering. SAP S/4HANA Cloud is a “Multi-Tenanted” platform, delivering highly standardized content for various lines of business in an industry and for varieties industries. As digital transformation sweeps the IT industry, embracing cloud technologies is inevitable. In this context, cloud security is imperative to this transformation.
SAP S/4HANA Cloud runs on public cloud such as Google Cloud Platform (GCP), MS Azure and SAP Converged Data Centres around the world. SAP uses hyperscale providers who offer “Infrastructure-as -a-Service for greater flexibility, scalability, and security for the provisioning of cloud infrastructure. SAP S/4HANA Cloud tenant subscription includes provisioning of SAP Business Technology Platform (BTP) services such as Identity Authentication Services, Identity Provisioning Service, SAP Analytics Cloud, and In-App & Side by side via BTP / Extensibility Framework. In an earlier blog, we discussed “RISE with SAP: Multi-layer Defence in Depth Architecture of SAP S/4HANA Cloud, Private Edition” . In this blog, we will discuss a conceptual view of a “multi-layered defense in depth” security architecture with SAP S/4HANA Cloud (Public cloud).
"Defense in Depth" Security Architecture:
SAP S/4HANA Cloud offers physical, technical, and administrative controls at various security layers. This cloud environment offers, secure by design and secure by default with highest standardization for the SaaS environment. The following diagram illustrates “multi-layer defense in depth” architecture of SAP S/4HANA Cloud.
Data Security
Customer Data Isolation:
Data Encryption:
Application Security
Network Security
Operational Security
The Cloud Operations and Management covers security patch management, hardening of operating systems, application, and databases virtual instances. The security incident and event management are available to collect, aggregate, correlate and apply security use cases for automatic alerts in the event of security incident occurrences. The team performs 24x7 infrastructure monitoring, database monitoring, secure admin access, regular backups, security vulnerability scanning, hacking simulations and remediations to secure the environment for customers.
The operational security activity broadly covers the following:
Secure Administration Access:
SAP Contractual Assurance:
SAP offers security assurance via contractual agreement, independent audits and certifications and having best practice security standards, policies, procedures. As a data processor, SAP cloud services comply to applicable data protection laws and provide personal data breach notifications without undue delay. The contractual agreements related to SAP cloud services can be downloaded at the SAP Trust Center. The Figure 4: SAP S/4HANA Cloud Security illustrates end-to-end security features.
Integration with SAP Business Technology Platform
SAP S/4HANA Cloud is integrating with SAP Business Technology Platform leveraging services such as Identity Authentication Services, Identity Provisioning Services and using integration suite and platform services. Customer can configure IAS (as IDP proxy), delegate authentications to their own IDP which may be located on-premises or in the cloud such Azure AD. The SAP BTP provides Identity Provisioning Services which allows synchronization of user data between source and target systems. SAP provides these services by default when customer subscribes to SAP cloud applications and it is the customer’s responsibility to configure these services depending on the authentication requirement
Audit and Compliance
SAP S/4HANA Cloud has achieved Certifications & Attestations on the following areas
SOC1 and SOC2 Type 2 audits are performed to validate design of security controls and implementation effectiveness of the security controls. SOC2 Type 2 report can be directly requested to SAP Trust Center subject to NDA. SOC1 Type 2 reports are available for existing customers who have production instance and have a valid NDA which can be requested via SAP Trust Center.
Shared Security Responsibility Model:
The security responsibility (as with any cloud services) is always shared between SAP (Cloud Service Provider) and cloud consumer. In SAP S/4HANA Cloud, customer have no access at the lower-level infrastructure layers such as VMs, Operating Systems, Load Balancers, Networking since this is fully managed by SAP. The following diagram illustrates shared security responsibility model between SAP and Cloud Customer.
Please refer to the blog “RISE with SAP: Shared Security Responsibility for SAP Cloud Services” for details. Specifically for SAP S/4HANA Cloud, the security control in the cloud stack is depicted in the diagram below:
Conclusion
The SAP S/4HANA Cloud offers highly standardized multi-tenanted landscape at a cost effective, scalable, defense in depth security at multiple layers. SAP S/4HANA Cloud operations adherence to best practice security is in alignment industry standards at technology, operational, legal measures. SAP handles critical security tasks such as secure architecture, security monitoring, security incident management, vulnerability scans, hacking simulations, independent 3rd party security audits, 24x7 Cyber SOC, This enables customers to focus on their core business processes and have a greater control over their data, reducing their total cost of ownership, enabling faster time to market.
(Disclaimer: The perspectives or opinions expressed in this blog are for information purposes only and should not be construed as a legal advice. The content in this blog does not constitute any representation, or any commitment or legal obligation on the part of SAP)
Introduction
The SAP S/4HANA Cloud is at the core of “Rise with SAP” offering. For a customer, it holds mission critical data used to implement business processes and data analytics. It is deployed in a public cloud as SaaS (Software-as-a-Service) offering. SAP S/4HANA Cloud is a “Multi-Tenanted” platform, delivering highly standardized content for various lines of business in an industry and for varieties industries. As digital transformation sweeps the IT industry, embracing cloud technologies is inevitable. In this context, cloud security is imperative to this transformation.
SAP S/4HANA Cloud runs on public cloud such as Google Cloud Platform (GCP), MS Azure and SAP Converged Data Centres around the world. SAP uses hyperscale providers who offer “Infrastructure-as -a-Service for greater flexibility, scalability, and security for the provisioning of cloud infrastructure. SAP S/4HANA Cloud tenant subscription includes provisioning of SAP Business Technology Platform (BTP) services such as Identity Authentication Services, Identity Provisioning Service, SAP Analytics Cloud, and In-App & Side by side via BTP / Extensibility Framework. In an earlier blog, we discussed “RISE with SAP: Multi-layer Defence in Depth Architecture of SAP S/4HANA Cloud, Private Edition” . In this blog, we will discuss a conceptual view of a “multi-layered defense in depth” security architecture with SAP S/4HANA Cloud (Public cloud).
"Defense in Depth" Security Architecture:
SAP S/4HANA Cloud offers physical, technical, and administrative controls at various security layers. This cloud environment offers, secure by design and secure by default with highest standardization for the SaaS environment. The following diagram illustrates “multi-layer defense in depth” architecture of SAP S/4HANA Cloud.

Figure 1: Multi-Layer Defence in Depth Security Architecture
Data Security
Customer Data Isolation:
- A virtualized ABAP Application Server is provisioned for each customer tenant
- Application isolation is enabled via “Security Group”
- The “Security Group” allows communication between different application instances that belongs to one tenant.
- Tenant “Security group” allows system communication between Q and P system of the same customer as shown in Figure 2 – SAP S/4HANA Landscape Cloud Architecture
- At the network level, security group prevents communication between tenants. The network traffic rules are defined using on source, destination, protocol, and ports
- Each SAP S/4HANA cloud tenant has their own tenant-database. It is part of overall SAP HANA Systems.
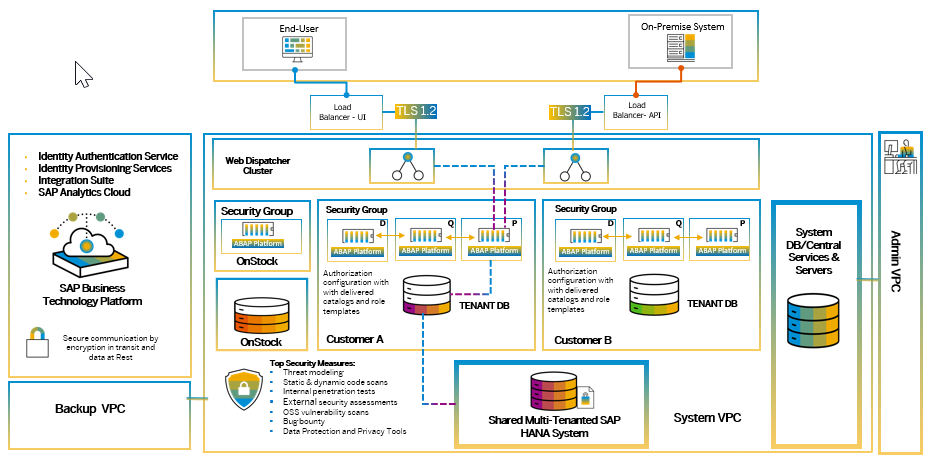
Figure 2: SAP S/4HANA Landscape Cloud Architecture
Data Encryption:
- SAP S/4HANA Cloud encrypts “data-at-rest” and “data-in-transit”
- End-to-end encryption is applied for “data-in-transit”
- “Data-at-rest” encryption covers database, central and local file systems, and storage backups.
- The cryptographic keys are managed securely via Key Management Systems (KMS) by SAP cloud operations teams
- “Segregation of Duties” guideline is applied for KMS.
Application Security
- Secure Software Development Lifecycle (SSDLC) methodology is followed for the development of SAP S/4HANA application
- The product development considers security and data protection & privacy requirements. This is embedded at the start of the development process.
- The development team performs extensive risk assessment and threat modelling, design, and test effectiveness of the security controls which includes performing code scans, penetration tests, security tests – SAST & DAST and independent security assessments. More details on SAP SSDLC can be found here.
- Customer access SAP S/4HANA Cloud via Internet using HTTPS (port 443). The HTTPS traffic is terminated on the Web Dispatcher cluster.
- Customer access is enabled via central load balancer and using shared web dispatcher. There are separate Load Balancer Endpoints for UI end point by business user and an endpoint used for system-to-system communications.
- Customer can access Application Security Audit Logs.
Network Security
- A trust boundary separates network into zones and each zone into segments.
- The security control is implemented into each zone based on the exposure of the systems to Internet/Intranet and is based on the classification of data handled by the systems in the zones.
- Virtual Private Cloud (VPC) is created for Systems, Admin, Backup. The system VPC is implemented to host the tenants of SAP S/4HANA cloud which spans availability zones. The secure central administration network segment host central cloud lifecycle management tools

Figure 3: High Level view of VPC segregation
Operational Security
The Cloud Operations and Management covers security patch management, hardening of operating systems, application, and databases virtual instances. The security incident and event management are available to collect, aggregate, correlate and apply security use cases for automatic alerts in the event of security incident occurrences. The team performs 24x7 infrastructure monitoring, database monitoring, secure admin access, regular backups, security vulnerability scanning, hacking simulations and remediations to secure the environment for customers.
The operational security activity broadly covers the following:
- SAP S/4HANA Cloud Infrastructure setup
- Data Segregation
- Intrusion Prevention
- Business Continuity & DR
- Secure Design of Cloud Services
- Network and Customer Segregation
- Backup and Restore Services
- Secure Development of platform services & tools
- Securing the infrastructure, operating systems, and/or container images, networking, and applications
- Operational and security monitoring
- Managing security incidents
- Personal Data Breach Notification
- Capacity Management
- Providing patches and solution support
- Vulnerability Scans, Hacking Simulations and Remediations
Secure Administration Access:
- SAP Cloud Administrator is allowed from whitelisted IP address and Multi-Factor Authentication sis required
- Security Groups enables communication between systems and admin VPC
- SAP uses central lifecycle management tools for operations and management of the cloud systems.
SAP Contractual Assurance:
SAP offers security assurance via contractual agreement, independent audits and certifications and having best practice security standards, policies, procedures. As a data processor, SAP cloud services comply to applicable data protection laws and provide personal data breach notifications without undue delay. The contractual agreements related to SAP cloud services can be downloaded at the SAP Trust Center. The Figure 4: SAP S/4HANA Cloud Security illustrates end-to-end security features.

Figure 4 - SAP S/4HANA Cloud - Cloud Security Summary
Integration with SAP Business Technology Platform
SAP S/4HANA Cloud is integrating with SAP Business Technology Platform leveraging services such as Identity Authentication Services, Identity Provisioning Services and using integration suite and platform services. Customer can configure IAS (as IDP proxy), delegate authentications to their own IDP which may be located on-premises or in the cloud such Azure AD. The SAP BTP provides Identity Provisioning Services which allows synchronization of user data between source and target systems. SAP provides these services by default when customer subscribes to SAP cloud applications and it is the customer’s responsibility to configure these services depending on the authentication requirement

Figure 5: Identity Authentication and Provisioning Service with SAP BTP
Audit and Compliance
SAP S/4HANA Cloud has achieved Certifications & Attestations on the following areas
- ISO Certificates
- ISO27001 Information Security Management System
- ISO27017 Implementation of cloud specific information security controls
- ISO27018 Protection of personal data in the cloud
- ISO22301 Business Continuity
SOC1 and SOC2 Type 2 audits are performed to validate design of security controls and implementation effectiveness of the security controls. SOC2 Type 2 report can be directly requested to SAP Trust Center subject to NDA. SOC1 Type 2 reports are available for existing customers who have production instance and have a valid NDA which can be requested via SAP Trust Center.
Shared Security Responsibility Model:
The security responsibility (as with any cloud services) is always shared between SAP (Cloud Service Provider) and cloud consumer. In SAP S/4HANA Cloud, customer have no access at the lower-level infrastructure layers such as VMs, Operating Systems, Load Balancers, Networking since this is fully managed by SAP. The following diagram illustrates shared security responsibility model between SAP and Cloud Customer.
Please refer to the blog “RISE with SAP: Shared Security Responsibility for SAP Cloud Services” for details. Specifically for SAP S/4HANA Cloud, the security control in the cloud stack is depicted in the diagram below:

Figure 6: Shared Security Responsibility
Conclusion
The SAP S/4HANA Cloud offers highly standardized multi-tenanted landscape at a cost effective, scalable, defense in depth security at multiple layers. SAP S/4HANA Cloud operations adherence to best practice security is in alignment industry standards at technology, operational, legal measures. SAP handles critical security tasks such as secure architecture, security monitoring, security incident management, vulnerability scans, hacking simulations, independent 3rd party security audits, 24x7 Cyber SOC, This enables customers to focus on their core business processes and have a greater control over their data, reducing their total cost of ownership, enabling faster time to market.
(Disclaimer: The perspectives or opinions expressed in this blog are for information purposes only and should not be construed as a legal advice. The content in this blog does not constitute any representation, or any commitment or legal obligation on the part of SAP)
Labels:
5 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
Artificial Intelligence (AI)
1 -
Business Trends
363 -
Business Trends
29 -
Customer COE Basics and Fundamentals
1 -
Digital Transformation with Cloud ERP (DT)
1 -
Event Information
461 -
Event Information
27 -
Expert Insights
114 -
Expert Insights
181 -
General
1 -
Governance and Organization
1 -
Introduction
1 -
Life at SAP
415 -
Life at SAP
2 -
Product Updates
4,682 -
Product Updates
261 -
Roadmap and Strategy
1 -
Technology Updates
1,500 -
Technology Updates
97
Related Content
- SAP Activate Realize and Deploy phase activities in the context of Scaled Agile Framework in Enterprise Resource Planning Blogs by SAP
- Why YCOA? The value of the standard Chart of Accounts in S/4HANA Cloud Public Edition. in Enterprise Resource Planning Blogs by SAP
- Shared Trouble is security doubled: the shared responsibility model for SAP S/4HANA Cloud in Enterprise Resource Planning Blogs by SAP
- SAP S/4HANA Cloud Public Edition Integration Extensibility FAQ-1 in Enterprise Resource Planning Blogs by SAP
- INFLUENCE THE DEVELOPMENT OF SAP ENTERPRISE THREAT DETECTION, CLOUD EDITION in Enterprise Resource Planning Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 10 | |
| 6 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |