
- SAP Community
- Products and Technology
- Enterprise Resource Planning
- ERP Blogs by Members
- SAP private linky swear with Azure – how to setup ...
Enterprise Resource Planning Blogs by Members
Gain new perspectives and knowledge about enterprise resource planning in blog posts from community members. Share your own comments and ERP insights today!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Martin-Pankraz
Active Contributor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-01-2021
5:18 PM
This post is part 7 of a series sharing service implementation experience and possible applications. Find the table of contents and my curated news regarding series updates here. Find the associated GitHub repos here. |
🛈Note: SAP added guidance on how to bring your own domain and certificate for SAP Private Link. That would be more favourable than the self-signed certificate used as an example in this post. The overall guidance regarding SNI stays the same for your own domain and certificate though. Since the release of Azure Application Gateway for SAP Private Link you may simplifiy your architecture further and increase security with a managed web application firewall. See this post for reference. |
Dear community,
Continuing with the implementation journey of SAP Private Link Service (PLS) we will have a closer look at the new host name feature and finally close the loop on the end-to-end SSL setup.

Fig.1 pinkies being secured by SSL
Even though PLS is a private tunnel, it is a common practice to utilize transport layer encryption on all levels. Also keep in mind that the source of your communication in BTP originates from a shared environment.
Back to the issue at hand: Remember part 1, where the pinkie broke his swear and SSL peer verification failed for my private IP from BTP?

Back then I gave a short lookout how the different approaches to solve this look like. Quick recap:
- http instead of https
- Override SSL verifier in your CF app
- Configure TrustAll on your BTP Destination
Or setup a dedicated SSL handler. Another alternative is Server Name Indication. However, both options require host names. The workaround, while we were still using private IPs on BTP, was resolving through nip.io. Luckily as of Nov 24th we got upgraded to host names for PLS 😊
Let’s have a look at the moving parts
Once you create a new PLS and bind it to your app, you see the new fields. The property “additionalHostname” is a less stable but a shorter property (less than 63 characters) that may change for every new instance that you create. It considers that some cert providers have a domain name length limit.
The property “hostname” is considerably longer because it includes a subdomain consisting of a hash of the resource id from your own Azure subscription. That aspect makes it stable for that part of the name and allows the creation of wildcard certificates. So, even if you clean up the link on BTP or create multiple links to the same PLS on Azure, you can keep the same certificate. That reduces your maintenance overhead.

Fig.2 Screenshot of PLS hostname config
Using the new hostname value, you need to adjust all your destinations. Let’s start with the Basic Authentication scenario. Register the new host name from BTP on your SAP backend and import the certificate from your target into the trust store of the BTP destination service.

Fig.3 BTP Destination config without custom trust store
So, where do we get that certificate? That depends on if you are using an SAP WebDispatcher (WDisp) in front of our SAP backend or if you like to hit it directly. We will look at the WDisp option first because it offers access restrictions too. Given that it is currently the best option to design the communication channel. Have a look at part 6 for more details.
Configuring TLS with SAP Web Dispatcher
Continuing our setup journey, you need to either adjust your existing Personal Security Environment (PSE) “SAPSSLS” or create a new one using the WDisp Admin UI. Anticipating that you have existing trust setups and the desire to stay flexible going forward, I recommend creating an additional PSE for the purpose of handling PLS connections.
The Admin UI is reachable on “https://your -domain:<your ssl-port>/sap/wdisp/admin/public/default.html”.
Next, you navigate to PSE Management and hit “Create New PSE”.

Fig.4 Screenshot of SAP WebDispatcher Admin UI to create new PSEs
Give it a meaningful file name following the SAP naming conventions. Have a look at the SAP docs for more details.

Fig.5 Create new PSE screen
Under “Distinguished Name” you put your hostname collected from BTP earlier on using this pattern:
DNS=PLS-HOSTNAME, CN=PLS-HOSTNAME or
DNS=*.PLS-HOSTNAME, CN=*.PLS-HOSTNAME.
To reduce maintenance, I recommend creating a wild card certificate. However, you can’t combine with SNI now. WDisp accepts such configuration but ignores the SSL request.
That means you need to either configure a dedicated PSE per private link without SNI or re-use your existing setup with SNI but create certificates without wildcards. Refer to note 2527968 SSL WildCard Certificates for SNI for further details.
Let’s look at SNI first as shown in fig.5. As a result of that create process, you get a new environment including the trusted certificate. Next, you need to export the certificate for the BTP Destination trust store.

Fig.6 Screenshot of newly created PSE setup for PLS
I copied the encoded text and created a new file called “wdisp-pls-cert.cer” locally. Move back to the Destination config on BTP and upload your new certificate to the trust store.
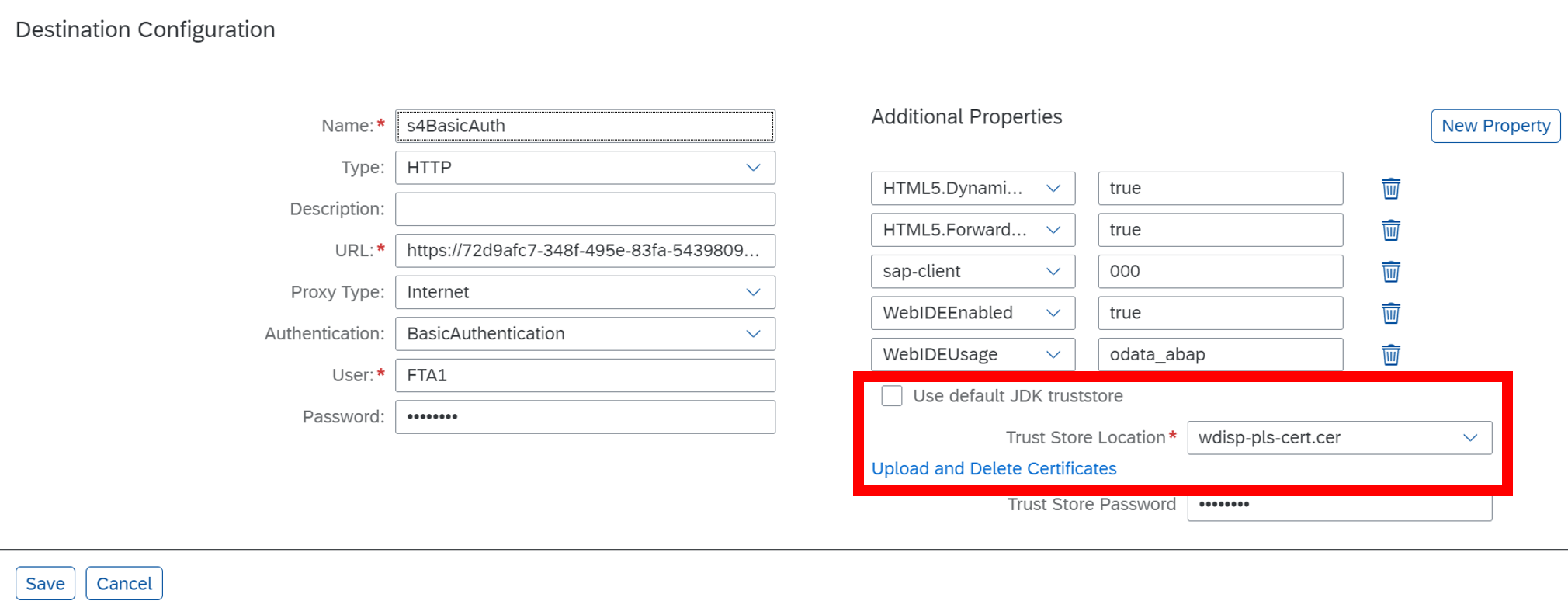
Fig.7 Destination config including certificate for PLS host name created through PSE
But how does the SAP WDisp know, which PSE to check for incoming traffic? I will describe two options:
1. Use SNI without wild card certitifcate
That challenge is addressed with the parameter option SNI_CREDS.

Fig.8 SAP Wdisp parameter config for SNI
For every incoming connection the WDisp evaluates the server’s name (in our case the PLS host name) and picks the certificate from the associated PSE.
2. Without SNI including wild card certificate
This approach requires enhancement of the server port (SSL listener) and its corresponding SSL config. The approach to adding a value and storing it is the same as shown in fig.8.

Fig.9 SAP WDisp config without SNI and wildcard certificate
I maintained an additional port with value 44310 and assigned the PSE that holds the wildcard certificate.

Fig.10 SAP WDisp config for PSE with wildcard certificate
Once you are done with either of the described options, trigger a restart of the WDisp (Core System >> Monitor >> Status >> Shutdown SAP Web Dispatcher). It comes up again by itself.
As mentioned before, you could also configure both options on the target ABAP server directly.
Configuration approaches for SSL with SAP NetWeaver directly
Given that the foundation for ICM, SNI etc. is identical between the WDisp and ABAP NetWeaver, you can re-use the files created by your WDisp.
The PSE needs to be stored in folder /usr/sap/<SID>/<instance>/sec on your ABAP system.
Using SAP GUI navigate to transaction SMICM >> GoTo >> Parameters >> Change. Identify your ICM setting “icm/ssl_config_0” and add SNI_CREDS accordingly. Note single spaces on ABAP config compared to WDisp config before. Find the official SAP docs for the param section here.
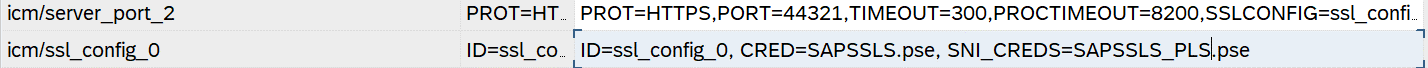
The same can be applied for the settings without SNI.
In case you are not going down the copy route from SAP WDisp, you will need to use the SAP CLI tool “sapgenpse”. Find the official docs and examples by SAP here. Of course, you also need a restart of the app server to load the new PSEs.
After that configuration marathon, we are ready for some testing 😊 as usual open the approuter target and navigate to the Java servlet associated with your Destination. As promised before, I am hitting the SAP Products with Basic Authentication, just as we did on the very first post of the series.
Et voilà ssl established end-to-end. Hurray!

Fig.11 Screenshot of OData result using end-to-end SSL config
Final Words
Uhh, that was quite the ride. I showed you today how you can finally enable end-to-end SSL encryption for your communication from BTP via PLS to your SAP backends. This approach was enabled by the hostname feature upgrade of PLS. In addition to that I explained the different approaches with the SAP WebDispatcher as a proxy and alternatively the ABAP backend directly.
I favour the SAP WebDispatcher, because of its URL filtering and access control capabilities. Furthermore, introducing wild card certificates is desirable to avoid certificate re-creation on PLS deletes, moves within subaccounts etc. or pointing multiple links at the same PLS on Azure.
You learned how you can apply Server Name Indication and SSL ports to enable a flexible and secure setup with BTP and PLS.
The next part of the blog series will discuss the differences between SAP Cloud Connector and SAP Private Link as this has been asked a lot.
Any further inputs from you @Developers and Security Experts?
@Kudos to Al Morrison and bobbiromsft for collaborating on the SNI setup 😊 it is always great fun and rewarding to work with you.
Find the related GitHub repos here. Find your way back to the table of contents of the series here.
Best Regards
Martin
- SAP Managed Tags:
- SAP BTP, Cloud Foundry runtime and environment,
- SAP Cloud SDK,
- SAP Connectivity service,
- SAP S/4HANA
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
"mm02"
1 -
A_PurchaseOrderItem additional fields
1 -
ABAP
1 -
ABAP Extensibility
1 -
ACCOSTRATE
1 -
ACDOCP
1 -
Adding your country in SPRO - Project Administration
1 -
Advance Return Management
1 -
AI and RPA in SAP Upgrades
1 -
Approval Workflows
1 -
Ariba
1 -
ARM
1 -
ASN
1 -
Asset Management
1 -
Associations in CDS Views
1 -
auditlog
1 -
Authorization
1 -
Availability date
1 -
Azure Center for SAP Solutions
1 -
AzureSentinel
2 -
Bank
1 -
BAPI_SALESORDER_CREATEFROMDAT2
1 -
BRF+
1 -
BRFPLUS
1 -
Bundled Cloud Services
1 -
business participation
1 -
Business Processes
1 -
CAPM
1 -
Carbon
1 -
Cental Finance
1 -
CFIN
1 -
CFIN Document Splitting
1 -
Cloud ALM
1 -
Cloud Integration
1 -
condition contract management
1 -
Connection - The default connection string cannot be used.
1 -
Custom Table Creation
1 -
Customer Screen in Production Order
1 -
Data Quality Management
1 -
Date required
1 -
Decisions
1 -
desafios4hana
1 -
Developing with SAP Integration Suite
1 -
Direct Outbound Delivery
1 -
DMOVE2S4
1 -
EAM
1 -
EDI
3 -
EDI 850
1 -
EDI 856
1 -
edocument
1 -
EHS Product Structure
1 -
Emergency Access Management
1 -
Energy
1 -
EPC
1 -
Financial Operations
1 -
Find
1 -
FINSSKF
1 -
Fiori
1 -
Flexible Workflow
1 -
Gas
1 -
Gen AI enabled SAP Upgrades
1 -
General
1 -
generate_xlsx_file
1 -
Getting Started
1 -
HomogeneousDMO
1 -
How to add new Fields in the Selection Screen Parameter in FBL1H Tcode
1 -
IDOC
2 -
Integration
1 -
Learning Content
2 -
LogicApps
2 -
low touchproject
1 -
Maintenance
1 -
management
1 -
Material creation
1 -
Material Management
1 -
MD04
1 -
MD61
1 -
methodology
1 -
Microsoft
2 -
MicrosoftSentinel
2 -
Migration
1 -
mm purchasing
1 -
MRP
1 -
MS Teams
2 -
MT940
1 -
Newcomer
1 -
Notifications
1 -
Oil
1 -
open connectors
1 -
Order Change Log
1 -
ORDERS
2 -
OSS Note 390635
1 -
outbound delivery
1 -
outsourcing
1 -
PCE
1 -
Permit to Work
1 -
PIR Consumption Mode
1 -
PIR's
1 -
PIRs
1 -
PIRs Consumption
1 -
PIRs Reduction
1 -
Plan Independent Requirement
1 -
Premium Plus
1 -
pricing
1 -
Primavera P6
1 -
Process Excellence
1 -
Process Management
1 -
Process Order Change Log
1 -
Process purchase requisitions
1 -
Product Information
1 -
Production Order Change Log
1 -
purchase order
1 -
Purchase requisition
1 -
Purchasing Lead Time
1 -
Redwood for SAP Job execution Setup
1 -
RISE with SAP
1 -
RisewithSAP
1 -
Rizing
1 -
S4 Cost Center Planning
1 -
S4 HANA
1 -
S4HANA
3 -
Sales and Distribution
1 -
Sales Commission
1 -
sales order
1 -
SAP
2 -
SAP Best Practices
1 -
SAP Build
1 -
SAP Build apps
1 -
SAP Cloud ALM
1 -
SAP Data Quality Management
1 -
SAP Maintenance resource scheduling
2 -
SAP Note 390635
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud private edition
1 -
SAP Upgrade Automation
1 -
SAP WCM
1 -
SAP Work Clearance Management
1 -
Schedule Agreement
1 -
SDM
1 -
security
2 -
Settlement Management
1 -
soar
2 -
Sourcing and Procurement
1 -
SSIS
1 -
SU01
1 -
SUM2.0SP17
1 -
SUMDMO
1 -
Teams
2 -
User Administration
1 -
User Participation
1 -
Utilities
1 -
va01
1 -
vendor
1 -
vl01n
1 -
vl02n
1 -
WCM
1 -
X12 850
1 -
xlsx_file_abap
1 -
YTD|MTD|QTD in CDs views using Date Function
1
- « Previous
- Next »
Related Content
- SAP Signavio Process Navigator turning 1-year old today! in Enterprise Resource Planning Blogs by SAP
- Quick Start guide for PLM system integration 3.0 Implementation/Installation in Enterprise Resource Planning Blogs by SAP
- Introducing the market standard of electronic invoicing for the United States in Enterprise Resource Planning Blogs by SAP
- Service with Advanced Execution and Resource-related Billing in Enterprise Resource Planning Blogs by SAP
- An introduction into Service Management in S/4HANA Cloud Private Edition in Enterprise Resource Planning Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |