
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Securing RISE with SAP S/4HANA cloud, private edit...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
03-20-2023
12:54 PM
(Jana Subramanian serves as APJ Principal Cybersecurity Advisor for Cloud Security and has been recognized as a Fellow of Information Privacy (FIP) by the International Association of Privacy Professionals (IAPP). As part of his responsibilities, Jana helps with strategic customer engagements related to topics such as cybersecurity, data privacy, multi-cloud security integration architecture, contractual assurance, audit, and compliance.)
Introduction
RISE with SAP S/4HANA Cloud, Private Edition (PCE) – Customer Data Center option is a cloud ERP solution that allows customers run SAP S/4HANA Cloud, private edition, on dedicated hardware in customer's own data centre or with Colocation services. This option caters to customers with data sovereignty, residency, and security requirements. It is particularly beneficial for customers in regions without Hyperscaler access, those requiring low-latency and high-performance, and those subject to strict regulations, as it allows customers to host their data and systems in their own data centre.
This blog discusses the high-level security measures in place for RISE with SAP S/4HANA Cloud, Private Edition deployed in a Customer Data Center (CDC).
Shared Security Responsibility
In simple terms, both SAP and the customer share the responsibility for security. SAP takes care of the reference architecture, infrastructure setup, configurations, operations, and management for the private managed environment. Meanwhile, the customer provides a certified data centre, handles internet access points, manages network access routing and security, and manage the SAP S/4HANA applications – functional & change management, data, and user access within the cloud environment.
The table below offers a high-level perspective on the shared security governance between SAP and customers.
Secure Network Access
Two internet VPN connections are established at the customer's internet access point:
Both these VPNs are encrypted and carry bi-directional management plane traffic to the RISE with SAP S/4HANA cloud, private edition, CDC.
The customer will provide the Public IPs for SAP to configure Admin Server within CDC environment. The VPN is essential for establishing the infrastructure and providing ongoing management and support. The customer is responsible for setting up and maintaining the VPN endpoints. Additionally, the customer can configure third-party devices between their data centre and the demarcation point of the Customer Data Center (CDC) to filter, control, or manage internet traffic as needed.
RISE with SAP S/4HANA cloud, private edition, customer data centre (CDC) option deployment will be and extension of customer's own internal network connected via redundant fibre / copper cross connect. Customer to provide IP ranges and DNS zone that are non-overlapping with the rest of their internal infrastructure, as per our CDC standards. Customer must provide all the firewall setups and controls on the network traffic to the CDC infrastructure.
Secure Architecture and Segregation
The detailed documentation on SAP S/4HANA cloud, private edition, customer data centre option – connectivity is available here. The salient security architecture details are as follows:
Access to Logs via LogServ (Optional)
LogServ is an SAP Enterprise Cloud Service (ECS) service designed to securely store and facilitate access to your own OS/DB, DNS, Network and Flow logs. SAP ECS platform enables both customers and internal teams to efficiently collect and centralize logs from all systems, applications, and ECS services in use. SAP ECS provides a secure API that allows authenticated access to customer-specific logs. Log data can be served in near real-time to multiple destinations, such as SIEM, data lakes, and customers, overall efficiency of log management. LogServ solution reduces the load on servers and data sources while offering additional features such as log filtering for cost optimization, log enrichment, and pseudonymization or anonymization of sensitive fields or data
Below is a high-level overview of the architecture for LogServ:
The Data Landing Zone (DLZ) is at the heart of LogServ's architecture, enabling SAP ECS to efficiently process and distribute log data to multiple destinations in the appropriate format. With DLZ, ECS can ensure that log data from a source is delivered to the right place at the right time securely. The salient feature of LogServ is that SAP ECS can offer near real-time log collection and integration with your SIEM or log management system. The log retention feature allows indefinite retention, with customizable retention policies for each data source. Longer retention periods are possible, and customer can also recover logs that were retained by SAP ECS.
Zero Trust Architecture Principles
The Zero Trust Architecture Framework changes traditional security methods by focusing on a flexible, identity-based approach instead of relying solely on perimeter defences and VPNs. Organizations need to protect various resources and manage access to them with dynamic policies that adapt to evolving threats. The NIST Special Publication (SP) 800-207 Zero Trust Framework explains these principles and provides examples of how zero trust can improve an enterprise's security.
You can refer to a blog titled "RISE with SAP: Adapting to Zero Trust Architecture Principles with SAP Cloud Services" to gain insights into how SAP adheres to Zero Trust Architecture principles when delivering SAP cloud services.
Multi-Layer Security
SAP employs a thorough multi-layer security strategy to protect its cloud services by incorporating security measures across multiple layers. This approach offers defence against threats at various levels, minimizing overall risk and bolstering the security of SAP environments.
1. Cloud Security Measures
In SAP cloud services, several security measures are implemented to protect data, applications, and infrastructure. These include data encryption, strong user authentication, access controls, network security, intrusion detection and prevention systems, regular security audits, vulnerability assessments, and compliance with relevant regulations and standards
2. Certification and Attestation
SAP collaborates with independent third-party auditors to verify the design of controls and the effectiveness of implementation, ensuring that SAP's cloud security controls, policies, and practices align with industry standards. Various certifications, audits, and assessments by these independent organizations maintain these assurances. Key attestations and assurances for SAP cloud services include ISO 27001, SOC 1 Type 2, SOC 2 Type 2, ISO 27017, ISO 27018, and many others, depending on the specific SAP cloud service. For details on the available certification and attestation, please refer to SAP Trust Center.
3. Technical and Organisation Measures
SAP has established a set of technical and organizational measures aimed at safeguarding personal data and complying with data protection regulations. The technical measures involve the implementation of encryption, access control, secure coding practices, among other protective measures that prevent unauthorized access or deletion of data. Meanwhile, the organizational measures encompass the protocols for handling personal data, developing incident response plans, security monitoring and notification of personal data breaches. These measures are contractually assured and can be referenced here.
4. Information Security Controls:
As part of commitment to information security, SAP adheres to the ISO 27002 as a baseline standard which provides a set of best practices for the development and implementation of an effective Information Security Management System (ISMS). This standard defines 14 information security controls such as security policy, access control, asset management, cryptography, and compliance. SAP conducts regular ISO27001 audits to ensure that its cloud services have robust ISMS put in place that protect information assets against unauthorized access, modification, or destruction. The standard covers all aspects of information security, including physical security, operations security, and supplier relationships. The ISO27001 certificates can be downloaded from SAP Trust Center
5. Trust Services Principles
SAP employs a set of principles developed by the American Institute of Certified Public Accountants (AICPA) to assess the effectiveness of controls in information systems. For cloud services, the appropriate Trust Services Principles (TSPs) are selected based on the relevance of the controls. These TSPs are used to evaluate the effectiveness of the design and implementation of the cloud service.
The TSPs consist of five principles that include:
Conclusion
This blog provides a high-level overview of the security features available for RISE with SAP S/4HANA Cloud, Private Edition, Customer Data Center options. While the customer is responsible for the qualified physical data centre, SAP employs security best practices in managing the landscape, ensuring data localization, data sovereignty, and regulatory compliance. As customer requirements can vary, it is recommended to engage with an SAP Cloud Architect Advisory for a thorough evaluation of each customer's security needs in order to develop approved solutions managed by SAP Enterprise Cloud Services. Alternatively, for additional inquiries, you may reach out to rakesh.roushan@sap.com.
Acknowledgement:
The author would like to express deep appreciation for Rakesh Roushan, Head of RISE with SAP S/4HANA cloud, private edition, customer data centre architecture & advisory and Roland Costea, Chief Information Security Officer, SAP Enterprise Cloud Services for their efforts in reviewing the content and providing valuable feedback.
Disclaimer:
© 2023 SAP SE or an SAP affiliate company. All rights reserved. See Legal Notice on www.sap.com/legal-notice for use terms, disclaimers, disclosures, or restrictions related to SAP Materials for general audiences.
Introduction
RISE with SAP S/4HANA Cloud, Private Edition (PCE) – Customer Data Center option is a cloud ERP solution that allows customers run SAP S/4HANA Cloud, private edition, on dedicated hardware in customer's own data centre or with Colocation services. This option caters to customers with data sovereignty, residency, and security requirements. It is particularly beneficial for customers in regions without Hyperscaler access, those requiring low-latency and high-performance, and those subject to strict regulations, as it allows customers to host their data and systems in their own data centre.
This blog discusses the high-level security measures in place for RISE with SAP S/4HANA Cloud, Private Edition deployed in a Customer Data Center (CDC).
Shared Security Responsibility
In simple terms, both SAP and the customer share the responsibility for security. SAP takes care of the reference architecture, infrastructure setup, configurations, operations, and management for the private managed environment. Meanwhile, the customer provides a certified data centre, handles internet access points, manages network access routing and security, and manage the SAP S/4HANA applications – functional & change management, data, and user access within the cloud environment.

Figure 1: Shared Security Responsibility Model
The table below offers a high-level perspective on the shared security governance between SAP and customers.
| Security Area | SAP | Customer |
| Identity and Authentication |
|
|
| Data Center and Infrastructure |
|
|
| Secure Access |
|
|
| Internet Access | Manage two internet VPN terminations at their internet access point:
|
|
| VPN |
|
|
| Infrastructure Setup |
|
|
| Operations |
|
|
Secure Network Access
Two internet VPN connections are established at the customer's internet access point:
- One connection originates from SAP's Customer Data Center (CDC) Shared Service Support Environment.
- The other connection comes from SAP's Infrastructure-as-a-Service (IaaS) Supplier Support Environment.
Both these VPNs are encrypted and carry bi-directional management plane traffic to the RISE with SAP S/4HANA cloud, private edition, CDC.

Figure 2: Secure Network Access
The customer will provide the Public IPs for SAP to configure Admin Server within CDC environment. The VPN is essential for establishing the infrastructure and providing ongoing management and support. The customer is responsible for setting up and maintaining the VPN endpoints. Additionally, the customer can configure third-party devices between their data centre and the demarcation point of the Customer Data Center (CDC) to filter, control, or manage internet traffic as needed.
RISE with SAP S/4HANA cloud, private edition, customer data centre (CDC) option deployment will be and extension of customer's own internal network connected via redundant fibre / copper cross connect. Customer to provide IP ranges and DNS zone that are non-overlapping with the rest of their internal infrastructure, as per our CDC standards. Customer must provide all the firewall setups and controls on the network traffic to the CDC infrastructure.
Secure Architecture and Segregation
The detailed documentation on SAP S/4HANA cloud, private edition, customer data centre option – connectivity is available here. The salient security architecture details are as follows:
- SAP S/4HANA Private Cloud Edition, customer data centre option is a single tenant deployment of S/4HANA in a dedicated physical hardware for each customer. The physical and virtual design is co-engineered with IaaS provider and approved by SAP. This is delivered as cloud operating, ran via your very own data centre saving significant upfront investment for customers.
- The landscape by default consists of 3 tier environments meant for development, quality assurance and production usage. The production and non-production environment segregated by a separate subnet, with an optional Network Access Controls.
- Infrastructure sizing is in general mapped to the license metrics. The infrastructure sizing based on the customer specific requirement will be done to assess the hardware capacity. Additional infrastructure can be deployed based on the actual needs of the customer via change order.
- As this is a private cloud offering, the dedicated network is created using customer provided private CIDR address range (RFC 1918 compliant) which is non-overlapping with customer’s on-premises network.
- RISE with SAP – Customer Data Center (CDC) is connected to the customer's internal network environment using at least 2 links (for redundancy) with a minimum speed of 10G per link. These links will carry all the network traffic to CDC (customer and management)
- Access to services from the public Internet is limited to specific use cases. To enable mobile users to access Fiori applications, a secure web application firewall can be used, and the customer is responsible for ensuring the firewall's availability. Cloud integrations are permitted to use secure protocols for outbound Internet connections (via customer network), and to connect to other SAP Cloud solutions, such as Ariba, Concur, and SuccessFactors.

Figure 3: Data Encryption
- Customer connects to dedicated SAP managed environment in Customer Own Data Center using dedicated cross connect network connection.
- Data-in-transit encryption is used to secure all client connections from Customer Network to SAP systems.
- All HTTP traffics are protected with TLS 1.2 transport layer encryption with AES-256-GCM
- Access from thick clients (SAP Frontend) is uses SAP proprietary DIAG protocol secured by SAP Secure Network Communication (SNC) with AES-256-GCM.
- SAP HANA in-memory database uses HANA Volume Encryption to provide “data-at-rest” encryption for data, log and backup volumes. It uses AES-256 encryption algorithm with Cipher block chaining (CBC) cipher mode (AES-256-CBC).
- Besides HANA volume encryption, persistent storage where SAP HANA stores encrypted volume is also encrypted using storage encryption modules (“data-at-rest” encryption). It also uses AES-256-GCM.
- A separate subnet can be allocated for both the production and non-production environments within the workload domain, ensuring a clear distinction and separation between the two.
Access to Logs via LogServ (Optional)
LogServ is an SAP Enterprise Cloud Service (ECS) service designed to securely store and facilitate access to your own OS/DB, DNS, Network and Flow logs. SAP ECS platform enables both customers and internal teams to efficiently collect and centralize logs from all systems, applications, and ECS services in use. SAP ECS provides a secure API that allows authenticated access to customer-specific logs. Log data can be served in near real-time to multiple destinations, such as SIEM, data lakes, and customers, overall efficiency of log management. LogServ solution reduces the load on servers and data sources while offering additional features such as log filtering for cost optimization, log enrichment, and pseudonymization or anonymization of sensitive fields or data
Below is a high-level overview of the architecture for LogServ:
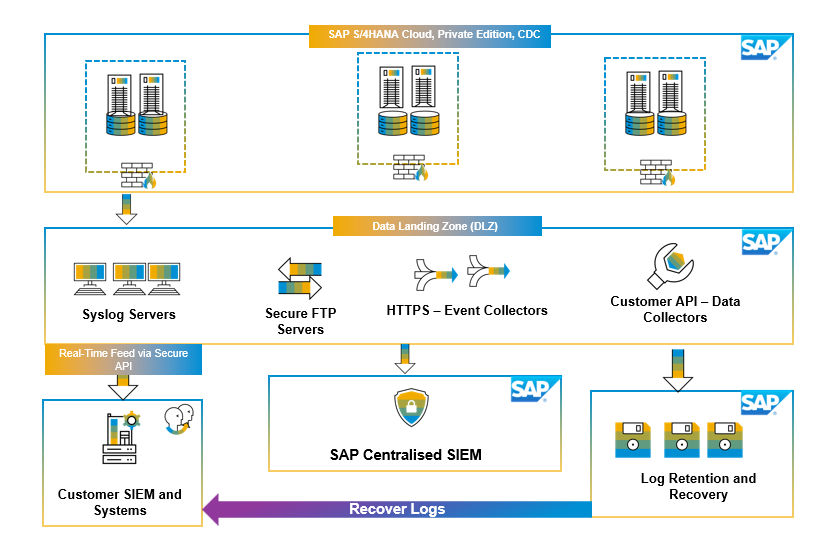
Figure 4: LogServ Architecture Overview
The Data Landing Zone (DLZ) is at the heart of LogServ's architecture, enabling SAP ECS to efficiently process and distribute log data to multiple destinations in the appropriate format. With DLZ, ECS can ensure that log data from a source is delivered to the right place at the right time securely. The salient feature of LogServ is that SAP ECS can offer near real-time log collection and integration with your SIEM or log management system. The log retention feature allows indefinite retention, with customizable retention policies for each data source. Longer retention periods are possible, and customer can also recover logs that were retained by SAP ECS.
Zero Trust Architecture Principles
The Zero Trust Architecture Framework changes traditional security methods by focusing on a flexible, identity-based approach instead of relying solely on perimeter defences and VPNs. Organizations need to protect various resources and manage access to them with dynamic policies that adapt to evolving threats. The NIST Special Publication (SP) 800-207 Zero Trust Framework explains these principles and provides examples of how zero trust can improve an enterprise's security.

Figure 6: Zero Trust Architecture Principle
You can refer to a blog titled "RISE with SAP: Adapting to Zero Trust Architecture Principles with SAP Cloud Services" to gain insights into how SAP adheres to Zero Trust Architecture principles when delivering SAP cloud services.
Multi-Layer Security
SAP employs a thorough multi-layer security strategy to protect its cloud services by incorporating security measures across multiple layers. This approach offers defence against threats at various levels, minimizing overall risk and bolstering the security of SAP environments.
1. Cloud Security Measures
In SAP cloud services, several security measures are implemented to protect data, applications, and infrastructure. These include data encryption, strong user authentication, access controls, network security, intrusion detection and prevention systems, regular security audits, vulnerability assessments, and compliance with relevant regulations and standards

Figure 6: Multi-Layer Security
2. Certification and Attestation
SAP collaborates with independent third-party auditors to verify the design of controls and the effectiveness of implementation, ensuring that SAP's cloud security controls, policies, and practices align with industry standards. Various certifications, audits, and assessments by these independent organizations maintain these assurances. Key attestations and assurances for SAP cloud services include ISO 27001, SOC 1 Type 2, SOC 2 Type 2, ISO 27017, ISO 27018, and many others, depending on the specific SAP cloud service. For details on the available certification and attestation, please refer to SAP Trust Center.
3. Technical and Organisation Measures
SAP has established a set of technical and organizational measures aimed at safeguarding personal data and complying with data protection regulations. The technical measures involve the implementation of encryption, access control, secure coding practices, among other protective measures that prevent unauthorized access or deletion of data. Meanwhile, the organizational measures encompass the protocols for handling personal data, developing incident response plans, security monitoring and notification of personal data breaches. These measures are contractually assured and can be referenced here.
4. Information Security Controls:
As part of commitment to information security, SAP adheres to the ISO 27002 as a baseline standard which provides a set of best practices for the development and implementation of an effective Information Security Management System (ISMS). This standard defines 14 information security controls such as security policy, access control, asset management, cryptography, and compliance. SAP conducts regular ISO27001 audits to ensure that its cloud services have robust ISMS put in place that protect information assets against unauthorized access, modification, or destruction. The standard covers all aspects of information security, including physical security, operations security, and supplier relationships. The ISO27001 certificates can be downloaded from SAP Trust Center
5. Trust Services Principles
SAP employs a set of principles developed by the American Institute of Certified Public Accountants (AICPA) to assess the effectiveness of controls in information systems. For cloud services, the appropriate Trust Services Principles (TSPs) are selected based on the relevance of the controls. These TSPs are used to evaluate the effectiveness of the design and implementation of the cloud service.
The TSPs consist of five principles that include:
- Security: Protection of the system from unauthorized physical or logical access
- Availability: The system's availability for use as agreed upon
- Processing Integrity: The system's processing is accurate, timely, authorized, and complete
- Confidentiality: The protection of designated confidential information as agreed upon
- Privacy: The collection, use, retention, and disclosure of personal information conform with the applicable privacy principles.

Figure 7: End-to-End Security
Conclusion
This blog provides a high-level overview of the security features available for RISE with SAP S/4HANA Cloud, Private Edition, Customer Data Center options. While the customer is responsible for the qualified physical data centre, SAP employs security best practices in managing the landscape, ensuring data localization, data sovereignty, and regulatory compliance. As customer requirements can vary, it is recommended to engage with an SAP Cloud Architect Advisory for a thorough evaluation of each customer's security needs in order to develop approved solutions managed by SAP Enterprise Cloud Services. Alternatively, for additional inquiries, you may reach out to rakesh.roushan@sap.com.
Acknowledgement:
The author would like to express deep appreciation for Rakesh Roushan, Head of RISE with SAP S/4HANA cloud, private edition, customer data centre architecture & advisory and Roland Costea, Chief Information Security Officer, SAP Enterprise Cloud Services for their efforts in reviewing the content and providing valuable feedback.
Disclaimer:
© 2023 SAP SE or an SAP affiliate company. All rights reserved. See Legal Notice on www.sap.com/legal-notice for use terms, disclaimers, disclosures, or restrictions related to SAP Materials for general audiences.
Labels:
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
110 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
74 -
Expert
1 -
Expert Insights
177 -
Expert Insights
348 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
14 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,575 -
Product Updates
391 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,871 -
Technology Updates
482 -
Workload Fluctuations
1
Related Content
- RingFencing & DeCoupling S/4HANA with Enterprise Blockchain and SAP BTP - Ultimate Cyber Security 🚀 in Technology Blogs by Members
- First steps to work with SAP Cloud ALM Deployment scenario for SAP ABAP systems (7.40 or higher) in Technology Blogs by SAP
- End-to-end Processes and modular processes in SAP Signavio Process Insights, discovery edition in Technology Blogs by SAP
- SAP BTP FAQs - Part 1 (General Topics in SAP BTP) in Technology Blogs by SAP
- B2B Business Processes - Ultimate Cyber Data Security - with Blockchain and SAP BTP 🚀 in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 15 | |
| 11 | |
| 10 | |
| 9 | |
| 8 | |
| 8 | |
| 7 | |
| 7 | |
| 7 | |
| 7 |