- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Handling Third Party Cookies Deprecation in Identi...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Background
A while ago Google announced the deprecation of third-party cookies for the Chrome-based browsers (Prepare for third-party cookie restrictions ). Starting Q1 2024, 1% of all browsers already have their third party cookies usage deprecated with the goal to completely phase out the old way of using cookies by mid-Q3 2024.
The Affected
As a result, certain sign-in scenarios concerning Single Sign-On (SSO) may be affected. Deprecating the traditional way of cookie usage means that browsers will automatically block cookies from applications embedded in inline frame (iframe), for example, thus braking sign-in flows. As Identity Authentication is often embedded on top-level pages, it had to ensure the SSO flow will continue to function. There are a couple of solutions that the administrators can implement after the start of the deprecation period.
The Solutions
Cookies Having Independent Partitioned State (CHIPS)
In this scenario, embedded applications can set partitioned cookies that can be used only on the current top-level site. The implementation of CHIPS depends on the developers of the given applications. The application has to be extended to support it. You can read more about that in Cookies Having Independent Partitioned State (CHIPS).
Storage Access API
This is also what Identity Authentication currently uses and supports. Read more at Storage Access API.
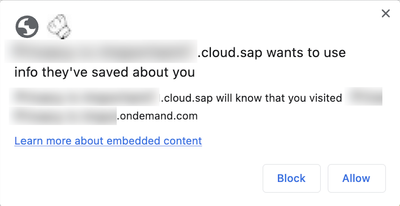
In the typical sign-in flow, the embedded application requests storage access permissions to the browser. Upon sign-in attempt, the user sees the following message: 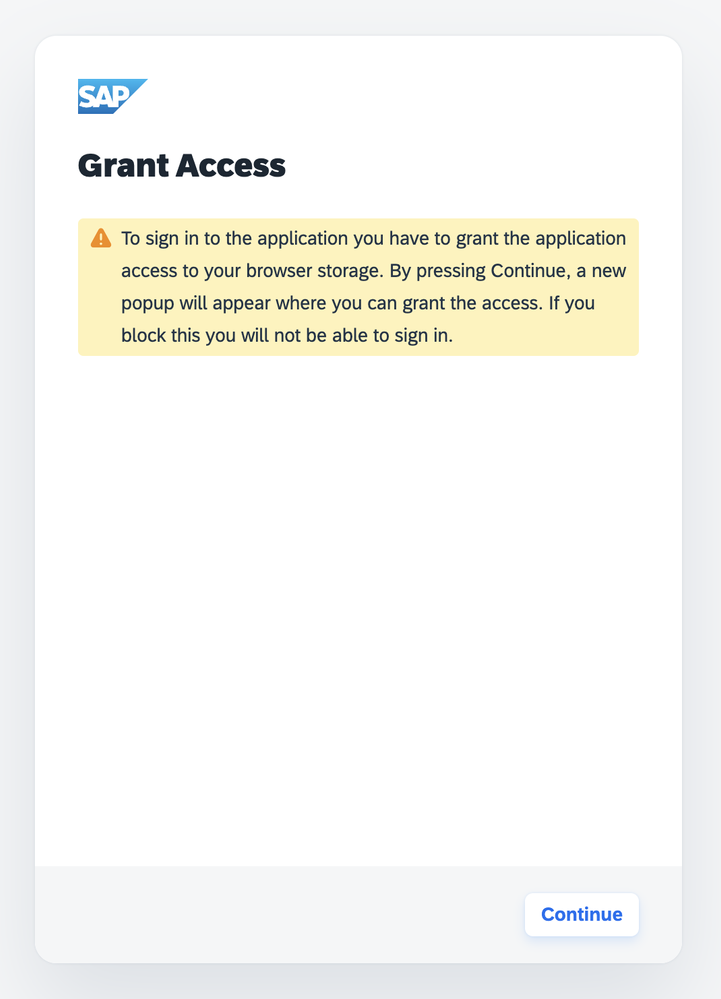
If access is allowed, the sign-in flow continues.
If denied, the sign-in flow of the embedded Identity Authentication sign-in screen is broken and no signing in is possible. The user sees the following message:
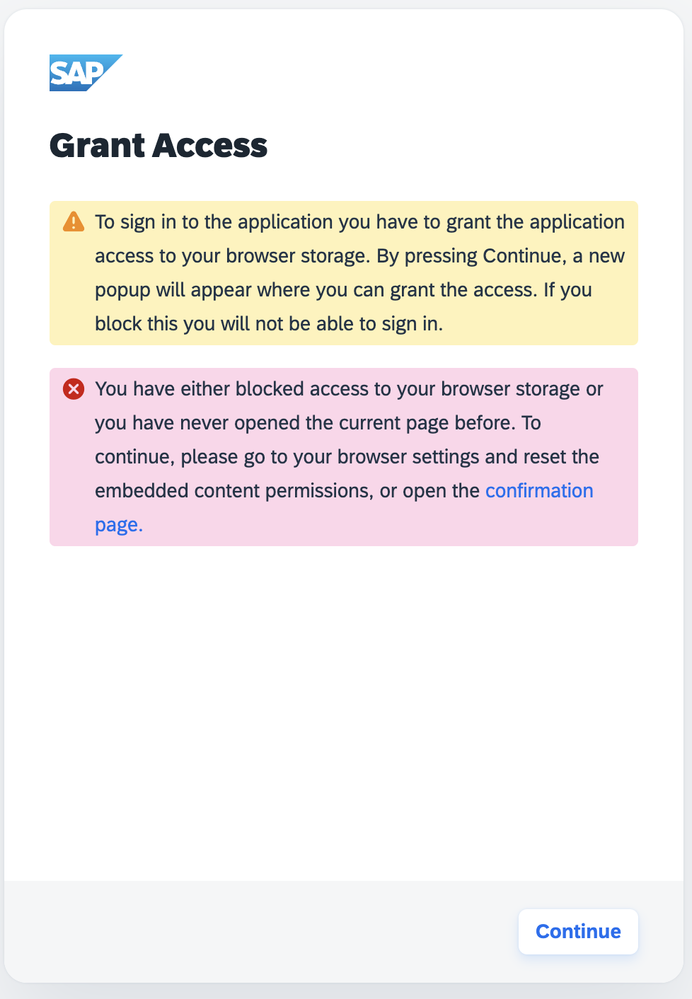
In another scenario, Identity Authentication can be used in a pure proxy mode. In this situation the browser of the user might have never interacted with the SAP (ondemand.com) domain. As a result, the browser blocks the iframed domain until the user interacts with it separately on a top-level.
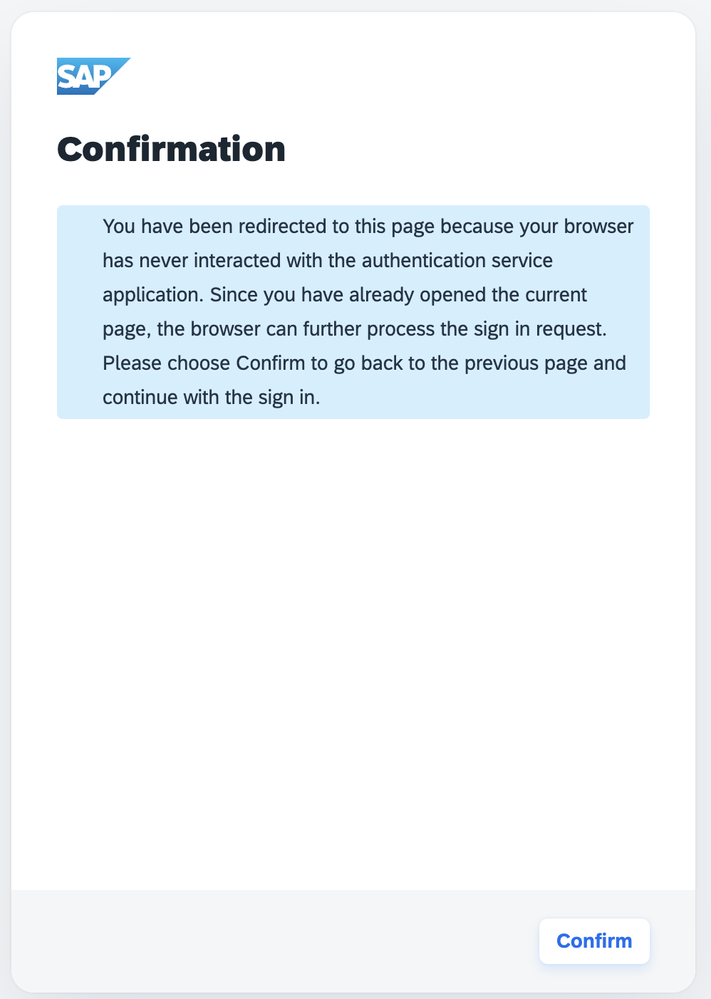
To resolve this, Identity Authentication redirects the users to a separate page, where they have to perform some kind of interaction, so that the top-level domain of the page is considered "familiar" to the browser. This interaction is as simple as the confirmation to the message below:
In some situations this might cause confusion, since with the proxy mode configuration the users might not even know they are signing in via Identity Authentication, or that SAP is involved in the sign-in flow at all. However, there was no other option to work around the limitation than sending the user to a separate confirmation page. Once the interaction is done, the users no longer need to perform this step.
Deprecation Trial
Google Offering
For customers that would require more time to implement changes on their application, Google offers a grace period. During this grace period, an opt-out of the new way of handling cookies is possible. Customers can obtain their deprecation trial tokens from Google upon request. You can read more at Preserving critical user experiences.
Identity Authentication Solution
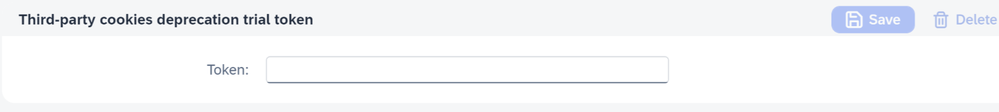
Identity Authentication supports such scenarios allowing customers to add their deprecation trial tokens so that they are sent via an HTTP header. This ensures that Identity Authentication customers with custom domains can use the deprecation trial for those domains respectively. The field to input the token is situated on the same place in the Identity Authentication admin console, where the custom domains are configured:
We will update this article if new updates or scenarios that we have not covered appear.
- SAP Managed Tags:
- SAP Cloud Identity Services
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
106 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
70 -
Expert
1 -
Expert Insights
177 -
Expert Insights
339 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
14 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,575 -
Product Updates
381 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,872 -
Technology Updates
470 -
Workload Fluctuations
1
- Enabling SAML Single Sign-On for SAP S/4 HANA and SAP BTP Apps using the same SAP IDP in Technology Blogs by SAP
- Streamlining User Provisioning from IBM Verify to SAP Cloud Identity Services in Technology Blogs by Members
- Embedding Business Context with the SAP HANA Cloud, Vector Engine in Technology Blogs by SAP
- Configuring SAP CI/CD pipeline for Deploying ReactJS application in Cloud Foundry in Technology Blogs by Members
- Sap Build Andriod app displays black screen after logging in in Technology Q&A
| User | Count |
|---|---|
| 17 | |
| 11 | |
| 7 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 6 | |
| 6 |