
- SAP Community
- Products and Technology
- Enterprise Resource Planning
- ERP Blogs by Members
- SAP S/4 ABAP SAML2 SSO with Cloud Identity Service...
Enterprise Resource Planning Blogs by Members
Gain new perspectives and knowledge about enterprise resource planning in blog posts from community members. Share your own comments and ERP insights today!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
BlackmanCC
Explorer
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2023 Jul 27
12:15 AM
4,833
- SAP Managed Tags:
- SAP S/4HANA
In this blog I explain how to setup Single Sign On for a (On Premise) S/4 HANA system with SAP Cloud Identity Services on BTP using SAML2. You can use this SSO for your Fiori Apps and other http services, e.g. WebGUI, not for SAP GUI.
We use Azure AD as a Corporate Identity provider in Cloud Identity Services. There are already some good blogs about this, e.g. Connecting SAP IAS as a proxy to Azure AD using OpenID Connect.
In our case we only do Single Sign On. The users in our system are already there and will not be created through Identity Propagation.
For troubleshooting please follow the guided answers under SAML 2.0 configuration or SAML 2.0 authentication does not work as expected. How can I troubleshoot ...
We use Azure AD as a Corporate Identity provider in Cloud Identity Services. There are already some good blogs about this, e.g. Connecting SAP IAS as a proxy to Azure AD using OpenID Connect.
In our case we only do Single Sign On. The users in our system are already there and will not be created through Identity Propagation.
- Get the SAML Metadata of your Cloud Identity Services Tenant


- Get the "Signing Certificate"In the same view you have to display the "Signing Certifcate". Please copy the "Certificate Information" String and put it in a text file, e.g. my_tenant_signing_cert.cer
 It would really be nice if SAP could deliver a "Get public key" button to get the needed information.
It would really be nice if SAP could deliver a "Get public key" button to get the needed information. - Export the public key of the "Signing Certificate", open the text file (double-click in Windows) and export the public key of the certificate (choose the first option "DER coded..."), filename e.g. public_key_my_tenant_signing_cert.cer.

- Enable the ABAP Platform as an SAML Service Provider
Call Transaction "SAML2" in your S/4 system

As a provider name choose what you want or system and client name e.g. SYS_100
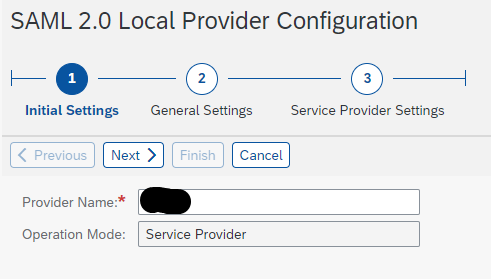
You should choose Selection Mode Automatic if you only have one Identity Provider connected, because you do not want to choose an Identity Provider every time.

Now you can download your Metadata of your SAML2 configuration in the S/4 client.

Create an "Application" for your S/4 HANA System

Now you have to upload the metadata.xml of your S/4 configuration to your SAML2 configuration in BTP Cloud Identity Service.

Please set all switches to ON.

In the section "Subject Name Identifier" please choose Email because we user Email for authentication.

In the section "Conditional Authentification" pleas choose your Coporate Identity provider

Please continue in your SAML2 configuration in S/4 and add your Identity Provider. You do this by uploading the XML-file you saved from your "Tenant Settings" in Cloud Identity Service.

For Metadata Verification please upload your public key.

Please enter an Alias for your provider which is shown when you should choose an Identity Provider. In our case this is not necessary because we only have one Identity Provider and switched on automatic selection before.

For better security choose SHA-256 instead of SHA-1

Please enter the "Supported NameID Formats" with the "Add" button. Choose "Uncpecified" and as "User ID Mapping Mode" Email. Please disable "Allow Identity Provider to create NameID" because in our case the users have you be already created in the system and we do not want that users without roles get created.

Please enable your "Trusted Provider".
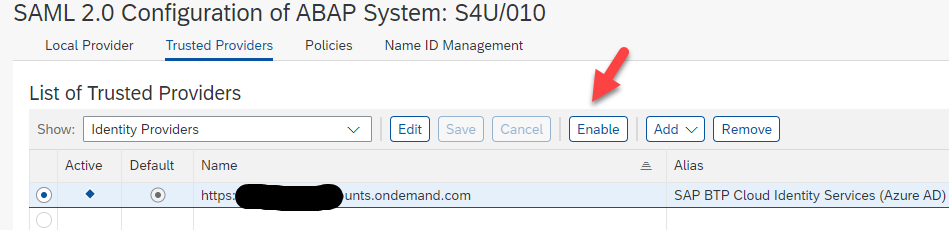
For troubleshooting please follow the guided answers under SAML 2.0 configuration or SAML 2.0 authentication does not work as expected. How can I troubleshoot ...
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
"Best Practice"
1 -
"mm02"
1 -
$session in CDS
1 -
*SAP"
1 -
- SAP
1 -
2023 Upgrade
1 -
@expertsap
2 -
@sapcommunity
1 -
A_PurchaseOrderItem additional fields
1 -
ABAP
5 -
abap cds
1 -
ABAP CDS VIEW
2 -
ABAP CDS Views
2 -
ABAP CDS Views - BW Extraction
1 -
ABAP CDS Views - CDC (Change Data Capture)
2 -
ABAP DDIC CDS view
1 -
ABAP Development
2 -
ABAP Extensibility
1 -
ABAP Programming
1 -
abapGit
1 -
ACCOSTRATE
1 -
ACDOCP
1 -
Adding your country in SPRO - Project Administration
1 -
Adobe form binding
1 -
Adobe forms
1 -
Adobe Printing
1 -
Advance Return Management
1 -
Advanced Intercompany Sales (5D2)
1 -
Advanced SAP Techniques
1 -
ADVANCED VARIANT CONFIGURATION
1 -
AgenticAI
1 -
AI and RPA in SAP Upgrades
1 -
API and Integration
1 -
Application Development for SAP HANA Cloud
1 -
Approval Workflows
1 -
Ariba
1 -
ARM
1 -
Artificial Intelligence (AI)
1 -
ASN
1 -
ASSET MANAGEMENT
1 -
Asset under construction
1 -
Assigned budget
1 -
Associations in CDS
1 -
Associations in CDS Views
2 -
Attachment List
1 -
auditlog
1 -
authorization
1 -
Auto PO from GR
1 -
Availability date
1 -
Azure Center for SAP Solutions
1 -
AzureSentinel
2 -
BADI
1 -
Bank
1 -
BAPI_PO_CREATE1
1 -
BAPI_SALESORDER_CREATEFROMDAT2
1 -
Best Practice
1 -
Billing
1 -
BRF+
1 -
BRFPLUS
1 -
Budget for PRs
1 -
Bundled Cloud Services
1 -
business participation
1 -
Business Partner Master Data
1 -
Business Processes
2 -
Business Trends
1 -
Business Trends
1 -
Capacity Planning
1 -
CAPM
1 -
Carbon
1 -
CDS Annotations
2 -
CDS View with Parameter
2 -
Cental Finance
1 -
Central finance
1 -
CFIN
2 -
CFIN Document Splitting
1 -
Charge calculation
1 -
Classical MRP
1 -
Cloud ALM
1 -
Cloud Integration
1 -
COGS SPLIT
1 -
Commitment Cost
1 -
Commitments by Cost Center
1 -
condition contract management
1 -
Condition Records
1 -
Condition technique
1 -
Connection - The default connection string cannot be used.
1 -
Consignment Process using MRP Area
1 -
Controlling
1 -
Conversion
1 -
CONVERSITON ECC TO S4HANA
1 -
COPA
1 -
Copy Control
1 -
Copy Inspection Results
1 -
cost distribution TM
1 -
Cost plan
1 -
CPI
1 -
CRM_PRICING_CUSTOMER_USER_EXIT
1 -
Custom Table Creation
1 -
Customer Screen in Production Order
1 -
Customizing
1 -
Data Analytics
1 -
Data Analytics & AI
1 -
Data Conversion
1 -
data migration
1 -
Data Quality Management
1 -
Date required
1 -
Decisions
1 -
desafios4hana
1 -
Developing with SAP Integration Suite
3 -
Direct Outbound Delivery
1 -
DMEEX
1 -
DMOVE2S4
1 -
DMS
1 -
DMS attachment Service SAP Object Link Tables
1 -
Downtime Optimization
1 -
DTW
1 -
DuplicateMasters
1 -
DuplicateMaterialMaster
1 -
EAM
2 -
ECTR
1 -
EDI
4 -
EDI 850
1 -
EDI 856
1 -
edocument
1 -
EHS Product Structure
1 -
Emergency Access Management
1 -
Employee Central Integration (Inc. EC APIs)
1 -
Energy
1 -
EPC
1 -
ERP
2 -
Expert Insights
1 -
Expert Insights
1 -
Extended Warehouse Management(EWM)
1 -
Finance
1 -
Financial Operations
1 -
Find
1 -
FINSSKF
1 -
fiori
1 -
FIORI MY-INBOX
1 -
Flexible Workflow
1 -
Forms & Templates
1 -
Freight Cost
1 -
FS
1 -
FTP
1 -
Functional Specification
1 -
Gas
1 -
GDPR
1 -
Gen AI enabled SAP Upgrades
1 -
General
2 -
generate_xlsx_file
1 -
Getting Started
1 -
GR Blocked stock
1 -
Group Reporting
1 -
GrowWithSAP
1 -
hardware specification
1 -
HomogeneousDMO
1 -
How to add new Fields in the Selection Screen Parameter in FBL1H Tcode
1 -
IAS
1 -
IAS-IPS
1 -
IDOC
2 -
Incompletion Log in Sales Order
1 -
innovation
1 -
INS
1 -
Inspection lot
1 -
Inspection Plan
1 -
Inspection Points
1 -
Integrated solution
1 -
Integration
1 -
Intercompany
1 -
Introducing SAP Analytics Cloud
1 -
InventoryAccounting
1 -
Investment Order
1 -
Just Ask
1 -
KE24
1 -
KEDR COPA Derivation
1 -
LE
1 -
Learning Content
2 -
Ledger Combinations in SAP
1 -
Life at SAP
1 -
LogicApps
2 -
LOVC
1 -
low touchproject
1 -
MAINTENANCE
1 -
management
1 -
Manufacturing
1 -
MasterDataGovernance
1 -
MasterDataManagement
1 -
Material creation
1 -
Material Management
1 -
MaterialMaster
1 -
MaterialMasterManagement
1 -
MD01N
1 -
MD04
1 -
MD61
1 -
MDG Derivation
1 -
methodology
1 -
Microsoft
2 -
MicrosoftSentinel
2 -
Migration
1 -
Migration Cockpit
1 -
mm purchasing
1 -
MRP
1 -
MRP Live
1 -
MS Teams
3 -
MT940
1 -
Multiple Valuation
1 -
Newcomer
2 -
Notifications
1 -
Oil
1 -
Oil & Gas
1 -
open connectors
1 -
OpenText Content Repository for QM Inspection Lots
1 -
Order Change Log
1 -
ORDERS
2 -
OSS Note 390635
1 -
outbound delivery
1 -
Output management in S4HANA
1 -
outsourcing
1 -
Overall budget exceeded error VS Annual budget exceeded error
1 -
OVR
1 -
Parallel Valuation
1 -
Payment medium
1 -
PCE
1 -
Permit to Work
1 -
Phase Model
1 -
PIR Consumption Mode
1 -
PIR's
1 -
PIRs
1 -
PIRs Consumption
1 -
PIRs Reduction
1 -
Plan Independent Requirement
1 -
PLM
1 -
PO Workbench
1 -
POSTMAN
1 -
poultry in s4hana
1 -
Premium Plus
1 -
pricing
1 -
Pricing Conditions
1 -
Primavera P6
1 -
Proactive Maintenance
1 -
Process Excellence
1 -
Process Management
1 -
Process Order Change Log
1 -
Process purchase requisitions
1 -
Procurement
1 -
Product Information
1 -
Product Updates
1 -
Production Order Change Log
1 -
Production Planning & Control
1 -
PROJECT SYSTEM
1 -
Purchase Blanket Agreement
1 -
purchase order
1 -
Purchase orders
1 -
Purchase requisition
1 -
Purchasing Lead Time
1 -
Putaway Strategy
1 -
QA32
1 -
Quality Inspection
1 -
Quantity Classification
1 -
QUERY SQL
1 -
Query View
1 -
Reactive Maintenance
1 -
Redwood for SAP Job execution Setup
1 -
Requirement Modeling
1 -
RFNO
1 -
RICEFW
1 -
RISE with SAP
2 -
RisewithSAP
2 -
Rizing
1 -
RPA
1 -
S4 Cost Center Planning
2 -
S4 FASHION
1 -
S4 HANA
1 -
s4 hana public cloud
1 -
s4hana
5 -
S4HANA Private Cloud
1 -
S4Hana Production Planning
1 -
S4HANACloud audit
1 -
S4HANAPrivateCloud
1 -
S4HANAPublicCloud
1 -
Sales and Distribution
1 -
Sales Commission
1 -
sales order
1 -
SAP
4 -
SAP ABAP RAP
1 -
SAP Basis
1 -
SAP Best Practices
1 -
SAP BTP Cloud Foundry
1 -
SAP Build
1 -
SAP Build Apps
1 -
SAP Business One
2 -
SAP Business One Service Layer
1 -
SAP CI
1 -
SAP Cloud ALM
1 -
SAP Cloud Integration
1 -
SAP CPI
1 -
SAP CPI (Cloud Platform Integration)
1 -
SAP Data Quality Management
2 -
SAP Digital Manufacturing for execution
1 -
sap DMS
1 -
SAP ECC
1 -
SAP ERP
2 -
SAP EWM
1 -
SAP Fiori Application
1 -
SAP Fiori Elements
1 -
SAP FSCM
1 -
sap gui
1 -
SAP HANA HA
1 -
SAP Integration Suite
1 -
SAP Integrations
1 -
SAP IS Retail
1 -
SAP IS-OIL
1 -
SAP JVA
1 -
SAP Maintenance resource scheduling
2 -
SAP Master data goverance
1 -
SAP MDG
1 -
SAP MDG Data Quality Management
1 -
SAP MDG DQM
1 -
SAP MDM
1 -
SAP Mentors
1 -
SAP MM
1 -
SAP Netweaver
1 -
SAP Note 390635
1 -
SAP PLM
1 -
SAP Post Refresh Steps
1 -
SAP Project System
1 -
SAP RAP
1 -
SAP S4 Finance.
1 -
SAP S4 HANA Conversion
1 -
SAP S4HANA
3 -
SAP S4HANA Cloud private edition
1 -
SAP S4HANA Public Cloud Finance
1 -
SAP Security
1 -
SAP Signavio
2 -
SAP Subcontracting Process
1 -
SAP Treasury and Risk Management
1 -
SAP Upgrade Automation
1 -
SAP WCM
1 -
SAP Work Clearance Management
1 -
SAP_CRM_JAVA_Pricing
1 -
SAPBTP
1 -
SAPDatasphere
1 -
Schedule Agreement
1 -
SCM-EWM
1 -
SCM-EWM-PMR
1 -
SD
1 -
SD (Sales and Distribution)
1 -
SD Pricing
1 -
SDM
1 -
Security
3 -
Settlement Management
1 -
Simulate
1 -
soar
2 -
software specification
1 -
Sourcing and Procurement
1 -
SSIS
1 -
Standard network determination according to organization parameters
1 -
Stock Transfer order
1 -
Storage location
1 -
String operations In CDS
1 -
SU01
1 -
SUM2.0SP17
1 -
SUMDMO
1 -
supply chain
1 -
Teams
2 -
Technology Updates
1 -
Test systems
1 -
Time Management
1 -
Transpo
1 -
Universal Parallel Accounting
1 -
Update Bill of Materials
1 -
upgrade
1 -
UsageofERP
1 -
UseageofSAP
1 -
User Administration
1 -
User Participation
1 -
UserAccess
1 -
UserInterface
1 -
utilities
1 -
va01
1 -
vendor
1 -
Vendor Rebates
1 -
vl01n
1 -
vl02n
1 -
Warehouse Management
1 -
WCM
1 -
Winshuttle
1 -
Work Center
1 -
X12 850
1 -
xlsx_file_abap
1 -
xml
1 -
xml_pretty_print
1 -
xmlviews
1 -
YTD|MTD|QTD in CDs views using Date Function
1
- « Previous
- Next »
Related Content
- Connecting SAP BTP and On-Premise SAP Business One using the SAP Cloud Connector in Enterprise Resource Planning Blogs by SAP
- Comparative Analysis of SAP PaPM: Standard Model vs. Universal Model. Nutshell. in Enterprise Resource Planning Blogs by SAP
- Resource Management Post 1KC Scope Item Deprecation in Enterprise Resource Planning Q&A
- Build Your Own Cash Sales Application with SAP Build Leveraging SAP S/4HANA Cloud Extensibility in Enterprise Resource Planning Blogs by SAP
- Artificial Intelligence and other Innovations in SAP S/4HANA Cloud Private Edition 2023 FPS02 in Enterprise Resource Planning Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |