
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- How to verify that the correct username is granted...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
former_member21
Explorer
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2017 Mar 14
4:01 AM
1,438
- SAP Managed Tags:
- SAP Mobile Services
To set up access to Mobile Service for Development and Operations cockpit from a SAP Cloud Platform account, please refer to the product documentation on “Setting Up Customer Accounts”.
When the SAP Cloud Platform account is switched from the use of Default SAP IdP to a custom Identity provider, access to the Mobile Service for Development and Operations cockpit results in a 403 error. The 403 error indicates that the authenticated user is not granted the required roles to access the cockpit.
Typically, following the steps outlined in “Setting Up Customer Accounts” resolves the issue. However, sometimes the root cause is that the username to which the roles are granted does not match the authenticated username based on the SAML assertion. In order to figure out the values included in the SAMLAssertion returned by the IdP to the Cloud Platform, one can use “SAML tracer” plugin in firefox or the equivalent “SAML Chrome Panel” for Chrome browser to look at the SAML Response in the network traffic to figure out the authenticated username in the SAMLAssertion to make sure the correct username is specified when granting the required roles.

After installing the plugin, lauch the SAML tracer plugin in Firefox or launch developer tools in chrome (by pressing F12) before accessing the Mobile Services Cockpit.

Now, navigate to the Mobile Services Cockpit url and when you get redirected to the IdP login page, enter valid user credentials to authenticate to the IdP. The SAML trace will contain the decoded SAML request from Mobile Services Cockpit to IdP.
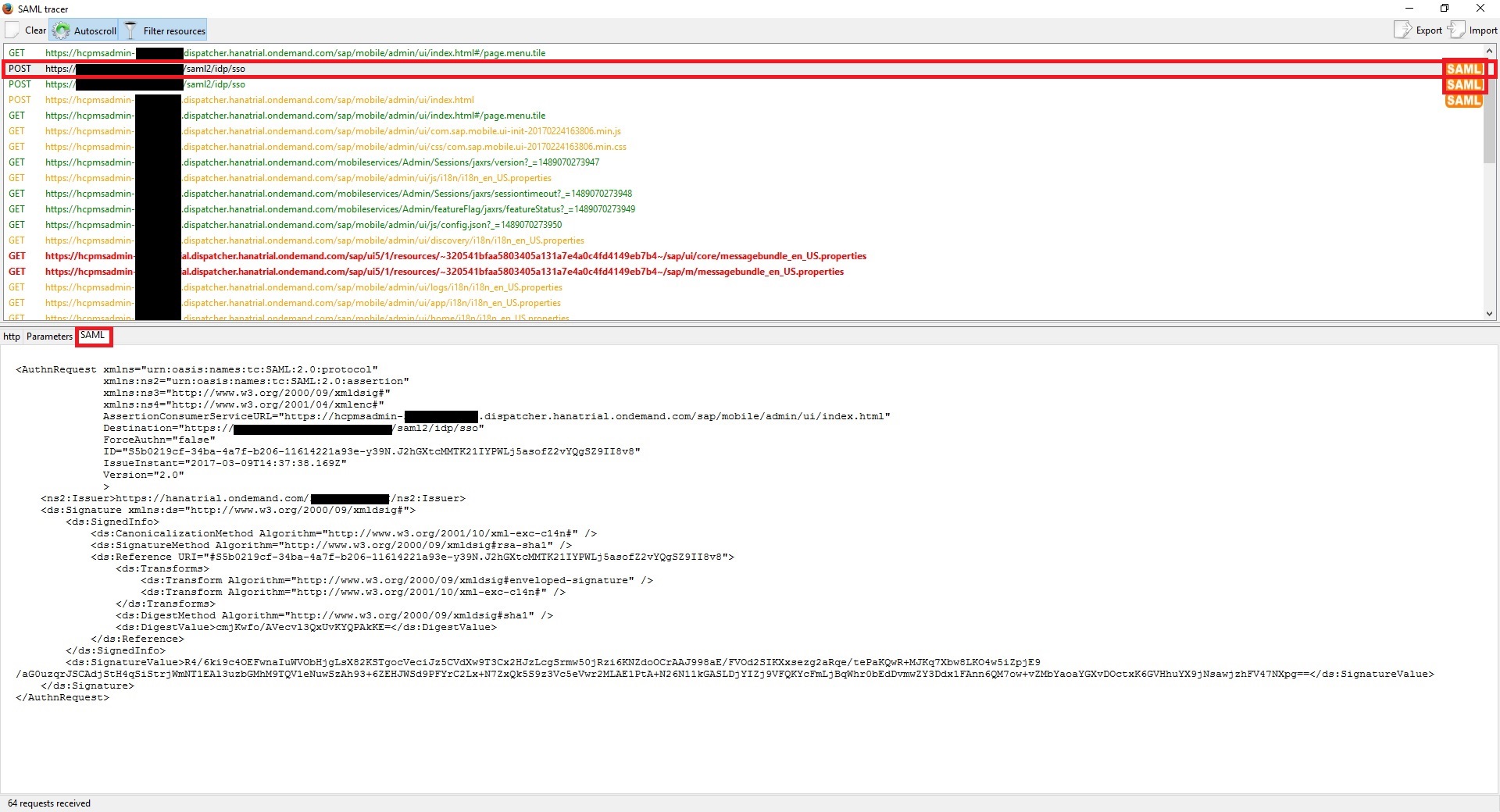
When redirected to the IdP login page, enter valid user credentials to authenticate to the IdP. Upon successful authentication, you will be redirected to Mobile Services Cockpit. At this point the SAML tracer will have captured the SAMLResponse posted from the IdP to the SAP Cloud Platform.

You can now examine the SAMLResponse to verify
Make sure that the username specified in the response matches the value you used to grant the required roles as specified in Setting Up Customer Accounts.
When the SAP Cloud Platform account is switched from the use of Default SAP IdP to a custom Identity provider, access to the Mobile Service for Development and Operations cockpit results in a 403 error. The 403 error indicates that the authenticated user is not granted the required roles to access the cockpit.
Typically, following the steps outlined in “Setting Up Customer Accounts” resolves the issue. However, sometimes the root cause is that the username to which the roles are granted does not match the authenticated username based on the SAML assertion. In order to figure out the values included in the SAMLAssertion returned by the IdP to the Cloud Platform, one can use “SAML tracer” plugin in firefox or the equivalent “SAML Chrome Panel” for Chrome browser to look at the SAML Response in the network traffic to figure out the authenticated username in the SAMLAssertion to make sure the correct username is specified when granting the required roles.

After installing the plugin, lauch the SAML tracer plugin in Firefox or launch developer tools in chrome (by pressing F12) before accessing the Mobile Services Cockpit.

Now, navigate to the Mobile Services Cockpit url and when you get redirected to the IdP login page, enter valid user credentials to authenticate to the IdP. The SAML trace will contain the decoded SAML request from Mobile Services Cockpit to IdP.

When redirected to the IdP login page, enter valid user credentials to authenticate to the IdP. Upon successful authentication, you will be redirected to Mobile Services Cockpit. At this point the SAML tracer will have captured the SAMLResponse posted from the IdP to the SAP Cloud Platform.

You can now examine the SAMLResponse to verify
- The authentication status reported by the IdP
- The intended recipient/audience of the response
- The username in the NameID field (If the IdP is configured to include other user details such as email address, firstname, lastname etc, they will be added as AssertionAttributes in the SAMLResponse. If you have configured any of those attributes to be the source of the authenticated username in the trusted IdP configuration in Cloud Platform account, then you can verify the value of those attributes.
Make sure that the username specified in the response matches the value you used to grant the required roles as specified in Setting Up Customer Accounts.
Labels:
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
Advanced Event Mesh
1 -
ai
1 -
Analyze Workload Data
1 -
BS Reclassification
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,657 -
Business Trends
213 -
CAP
1 -
cf
1 -
Characteristics display
1 -
Classes
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Databricks
1 -
Datasphere
2 -
Event Information
1,396 -
Event Information
173 -
Expert
1 -
Expert Insights
178 -
Expert Insights
743 -
General
2 -
Getting Started
2 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Introduction
1 -
Kafka
1 -
Life at SAP
779 -
Life at SAP
43 -
MDG materials
1 -
MDGM
1 -
Migrate your Data App
1 -
MLFlow
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,562 -
Product Updates
815 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
2 -
SAP Datasphere
2 -
SAP Datasphere تحقيق أقصى استفادة من بيانات الأعمال
1 -
SAP MDG Data Quality Management
1 -
SAP MDG DQM
1 -
SAP s4hana cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technical article
1 -
Technology Updates
6,864 -
Technology Updates
986 -
Workload Fluctuations
1
Related Content
- SAP MDK Failed to build the Offline OData in Technology Q&A
- How-To: Use Script Tasks in SAP Build Process Automation in Technology Blogs by SAP
- Analyzing and Managing Memory Consumption in SAP HANA in Technology Blogs by Members
- RAP Business Events with Advanced Event Mesh [1]: Connecting AEM to S/4HANA On Premise 2023 in Technology Blogs by SAP
- Integrate SAP Build Process Automation with Custom Business Object from S/4HANA Cloud in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 18 | |
| 13 | |
| 12 | |
| 11 | |
| 9 | |
| 8 | |
| 7 | |
| 6 | |
| 5 | |
| 5 |