
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- How to configure Azure AD for Principal Propagatio...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
former_member21
Participant
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-24-2019
7:25 AM
Hello Everyone
This blog aims to assist anyone that is trying to configure Principal Propagation scenario between SAP Cloud Platform and a backend system, but uses Azure as the Identity Provider.
The Principal Propagation method is very popular among customers and several times they use a custom IdP, like Azure.
When this happens, there are some adjustments that need to be made in order to properly send the attributes in the SAML that the SAP Cloud Connector will be able to recognize and use it to generate the X.509 certificate, used to authenticate the user in the backend.
As we can see in the help page (Configure a Subject Pattern for Principal Propagation), the SAP Cloud Connector expects four types of attributes when performing the Principal Propagation. They are the following:
So, when we are configuring a scenario like this, we need to make sure that at least one of the attributes above will be present in the SAML sent by the IDP.
In order to make the Azure include this attribute in the SAML, you need to do the following:
Now you have everything you need to go through the Principal Propagation configuration.
There is a good blog about it already, check it out: How to Guide – Principal Propagation in an HTTPS Scenario
You can also follow our official documentation:
Configure Principal Propagation to an ABAP System for HTTPS
Just remember the following differences:
Feel free to leave any comments or questions. I will be happy to answer.
Unable to generate authorization token for user <user> on system <system>:<port>
Cheers,
Augusto Ferreira
Support Engineer, SAP Product Support
This blog aims to assist anyone that is trying to configure Principal Propagation scenario between SAP Cloud Platform and a backend system, but uses Azure as the Identity Provider.
The Principal Propagation method is very popular among customers and several times they use a custom IdP, like Azure.
When this happens, there are some adjustments that need to be made in order to properly send the attributes in the SAML that the SAP Cloud Connector will be able to recognize and use it to generate the X.509 certificate, used to authenticate the user in the backend.
What you will need:
- SAP Cloud Platform account
- (Optional) SAP Cloud Platform Identity Authentication tenant
- Microsoft Azure AD
- SAP Cloud Connector
- Backend system (in this case we are going to use an ABAP)
Before you start:
- Make sure that your SAP Cloud Platform account is configured to trust the Azure AD or the Identity Authentication tenant (that trusts the Azure AD)
- Make sure your SAP Cloud Connector is synchronized with your SAP Cloud Platform account and also is synchronized with the Azure AD.
Configure Trusted Entities in the Cloud Connector
Configuration Steps:
- Add a new claim under User Attributes & Claims
- Test to see if the new parameter is now included on the SAML
- Follow the Principal Propagation configuration
1 - Add a new claim under User Attributes & Claims
As we can see in the help page (Configure a Subject Pattern for Principal Propagation), the SAP Cloud Connector expects four types of attributes when performing the Principal Propagation. They are the following:
- name
- display_name
- login_name
So, when we are configuring a scenario like this, we need to make sure that at least one of the attributes above will be present in the SAML sent by the IDP.
In order to make the Azure include this attribute in the SAML, you need to do the following:
- In your Azure account, go to Azure Active Directory -> Enterprise Applications
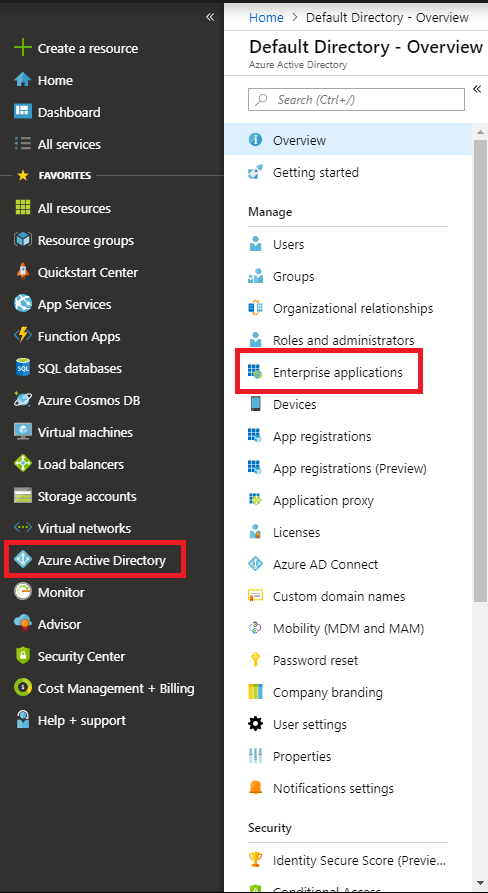
- All Applications -> SAP Cloud Platform Identity Authentication OR SAP Cloud Platform (depending if you are using the IAS tenant or the SCP directly)

- Single sign-on -> User Attributes & Claims

- Click on Add new claim

- Set the Name with one of the four values that the SAP Cloud Connector accepts (name, mail, display_name and login_name) and set the Source Attribute accordingly, then press Save

2 - Test to see if the new parameter is now included on the SAML
- Open your SAP Cloud Platform account
- Go to Services -> Web IDE Full-Stack
- Open the developer tools of the Chrome (F12)
- Select the SAML tab
- Click on Go to Service
- You will be redirected to the Azure login page.
Login with your user and password from Azure - You should be able to see the SAML traces recorded on the Chrome's DevTools.
- The attribute you included on Azure AD(in this case, login_name) should now be visible in the SAML as follows:

3 - Follow the Principal Propagation configuration
Now you have everything you need to go through the Principal Propagation configuration.
There is a good blog about it already, check it out: How to Guide – Principal Propagation in an HTTPS Scenario
You can also follow our official documentation:
Configure Principal Propagation to an ABAP System for HTTPS
Just remember the following differences:
- When synchronizing the IdP for Principal Propagation, remember that you will need to syncronize with your custom IDP (Azure AD)
- When configuring the certificates on SAP Cloud Connector, in the Principal Propagation section, use the attribute created on step 1 (the one you customized on Azure AD to include in the SAML).
That is it!
Feel free to leave any comments or questions. I will be happy to answer.
Error messages for discoverability:
Unable to generate authorization token for user <user> on system <system>:<port>
Cheers,
Augusto Ferreira
Support Engineer, SAP Product Support
- SAP Managed Tags:
- SAP Cloud Identity Services,
- SAP Connectivity service,
- SAP Business Technology Platform
Labels:
17 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
132 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,399 -
Event Information
95 -
Expert
1 -
Expert Insights
177 -
Expert Insights
431 -
General
2 -
Getting Started
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
18 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,571 -
Product Updates
481 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,868 -
Technology Updates
562 -
Workload Fluctuations
1
Related Content
- Failed to load destination. Caused by: No user token (JWT) has been provided. This is strictly neces in Technology Q&A
- NDC Financial Consolidation in Technology Blogs by Members
- Technical User Propagation from JCo towards On-Premises in Technology Blogs by SAP
- SAP BTP FAQs - Part 3 (Security) in Technology Blogs by SAP
- Single Sign On to SAP Cloud Integration (CPI runtime) from an external Identity Provider in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 21 | |
| 13 | |
| 10 | |
| 10 | |
| 9 | |
| 8 | |
| 7 | |
| 7 | |
| 7 | |
| 7 |