
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Configuring OAuth 2.0 with SAML Bearer in SAP Proc...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-03-2022
7:05 PM
Introduction
SAP SuccessFactors announced some time back the sunset of HTTP Basic Authentication for API calls. The sunset, which was planned for 2H 2022, was postponed until further notice. Nevertheless, SAP Process Orchestration SFSF adapter was enhanced to support OAuth 2.0 with SAML Bearer Assertion flow for OData API and SFAPI (see SAP Note 3111868 for more information). In this blog, we are going to see how we can configure a SAP Process Orchestration SFSF channel with OAuth 2.0.
Procedure
Before configuring the SFSF channel, you must register an OAuth client application in SAP SuccessFactors. The registration requires you to create a public and private key for the client and import the client's public certificate in SAP SuccessFactors. There are various ways for generating the key pair - using a trusted service provider, using a third-party tool to create a self-signed certificate, generating the key pair directly in SAP SuccessFactors (not recommended). We'll see how we can generate the key pair directly on the SAP Process Orchestration system and how to import the certificate in SAP SuccessFactors.
Generate the client key pair in SAP Process Orchestration
To generate public and private key in SAP Process Orchestration, open NetWeaver Administrator and navigate to Configuration - Security - Certificates and Keys.
1. (Optional) Add a new keystore view to hold the private key
2. Select the keystore view and press the "Create" button

3. Type a name for the entry and select the option "Store Certificate"

4. Fill in the Subject properties

5. (Optional) Select a signing key pair

6. Review the information and press "Finish"

7. Select the generated certificate and press "Export Entry"

8. Set the export format to Base64 X.509

9. Download the certificate to a file

Register the OAuth client in SAP SuccessFactors
1. Log on to SAP SuccessFactors Admin Center and open "Manage OAuth2 Client Applications"

2. Press "Register Client Application"

3. Enter the OAuth client details

Note: The Application URL is a unique URL of the page the client wants to show to the end user. This is used for 3-legged OAuth, however, it isn't currently supported
4. Open the downloaded certificate (Step 8 above) with a text editor and copy everything between the first and the last lines

5. Paste the copied content in the "X.509 Certificate" field on the OAuth client registration screen and press "Register"
6. Press the "View" button to view the registered OAuth client

7. Copy the API Key, which is used as Client ID

Configuring the SFSF channel
Open the SFSF channel configuration and set the Authentication Method to "OAuth 2.0"
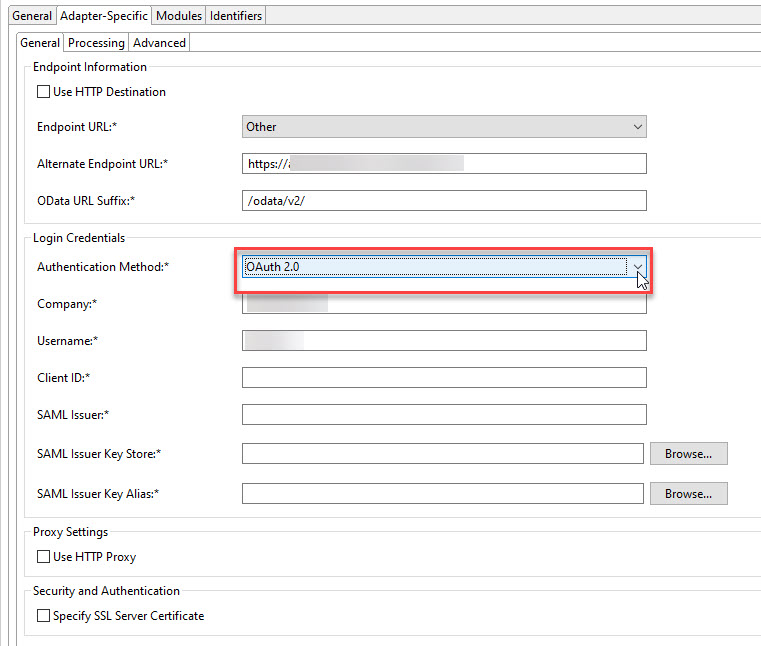
Fill in the properties:
- Company - your SAP SuccessFactors Company ID (used as company_id in the Access Token request)
- Username - the username you are using to access SAP SuccessFactors (used as Subject/NameID in the SAML Assertion)
- Client ID - the API Key generated during OAuth client registration (Step 7) (used as client_id in the Access Token request and as api_key Attribute in the SAML Assertion)
- SAML Issuer - issuer information of the SAML Assertion
- SAML Issuer Key Store - the key store view that holds the OAuth client private key
- SAML Issuer Key Alias - the OAuth client private key entry (used to sign the SAML Assertion)
The adapter will use the provided data to generate internally a SAML Assertion, which will then be used to request an access token.
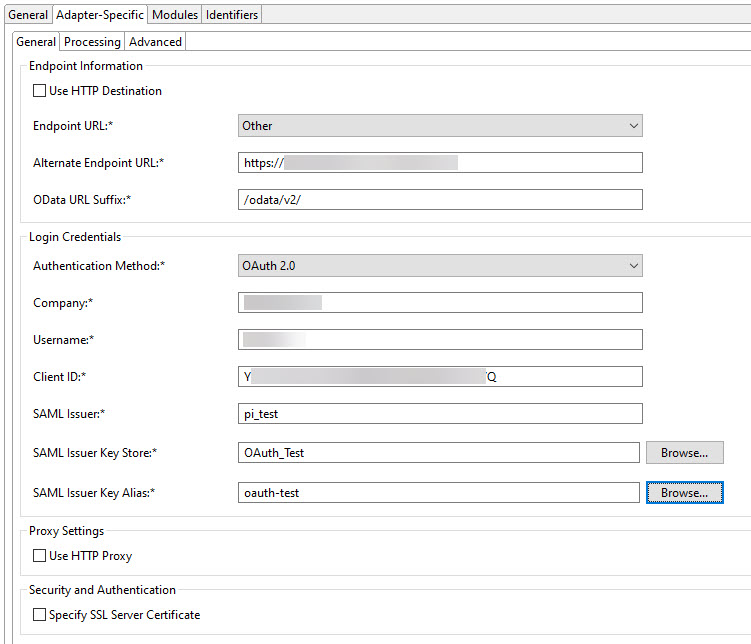
Note: If you are changing the authentication method of an existing channel from Basic Authentication to OAuth 2.0, the username and company will be pre-filled.
Troubleshooting
In case you face issues, related to SSL/TLS handshake during the access token request, refer to the following SAP Notes/KBAs:
2616423 - SSL does not work between PI and Remote System - SSLException: Peer sent alert: Alert Fata... (the example shown is for REST adapter, however, the symptom and solution are relevant)
3056954 - How to check the cipher suites enabled in SAP Process Integration system for outbound conn...
2708581 - ECC Support for Outbound Connections in SAP NW AS Java - SAP ONE Support Launchpad
Summary
In this blog we saw how to generate private key and certificate in SAP Process Orchestration to use in OAuth 2.0 with SAML Assertion flow. Then we saw how to register an OAuth2 client application in SAP SuccessFactors. Finally, having completed these prerequisites, we configured a SAP Process Orchestration SFSF channel using OAuth 2.0 with SAML Assertions as the authentication method.
Feel free to ask any questions or share your feedback in the comments. Follow SAP Process Integration and SAP Process Orchestration tags for updates.
Further reading
Configuring the SFSF Adapter | SAP Help Portal
SAP Process Integration Connectivity Add-on 2.0 | SAP Blogs
3091094 - SFSF/OData adapters become standard (FAQ) - SAP ONE Support Launchpad
3111868 - New Feature: Support for OAuth 2.0 with SAML Assertions in SFSF adapter - SAP ONE Support ...
Labels:
7 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
107 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
72 -
Expert
1 -
Expert Insights
177 -
Expert Insights
340 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
14 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,575 -
Product Updates
384 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,872 -
Technology Updates
472 -
Workload Fluctuations
1
Related Content
- SAP BTP FAQs - Part 1 (General Topics in SAP BTP) in Technology Blogs by SAP
- How to Leverage SAP CI and APIM for Hyperlink with Query Parameters as Input and no Authentication in Technology Blogs by Members
- SAP Datasphere + SAP S/4HANA: Your Guide to Seamless Data Integration in Technology Blogs by SAP
- SAP S/4HANAとSAP Datasphereのデータ連携 : DP Agentの設定 in Technology Blogs by SAP
- Deploying SAP S/4HANA Containers with Kubernetes in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 17 | |
| 14 | |
| 12 | |
| 10 | |
| 9 | |
| 8 | |
| 7 | |
| 7 | |
| 6 | |
| 6 |